
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
This session will assist you in setting up a new network on the EnGenius Cloud web application. For easier, faster setup, use the EnGenius Cloud for iOS or EnGenius Cloud for Android mobile apps. No matter which version you start with, you can always switch seamlessly between the web and mobile.
EnGenius Cloud is a modern cloud-based management platform, where teams manage wireless/wired network devices with a state-of-the-art visualized GUI and features for AI and serverless technologies.
Other Languages: 日本語
To start using the EnGenius Cloud service, you must prepare the following:
At least one supported EnGenius Cloud wireless access point or switch.
An existing network with an Internet connection including DHCP and DNS configuration.
The EnGenius Cloud is primarily accessible with a web browser. Before signing up for the EnGenius Cloud service or logging on to the web interface to manage your network, first verify that you are using a supported browser.
The following table lists the web browsers that EnGenius Cloud supports:
If you use an unsupported web browser, you may experience issues displaying elements on the web interface.
Browser
Release
Google Chrome
57.0.2987.110 and later
Mozilla Firefox
52.0 and later
Microsoft Edge
80.0.361.103 and later
VLAN pooling is a feature of EnGenius Cloud that allows you to split a large network into smaller virtual networks (VLANs) to reduce traffic and improve performance. To enable VLAN pooling, you need to select Dynamic Client VLAN Pooling in the WLAN settings and enter the VLAN IDs that you want to add to the pool.
Each client connected to the WLAN will be assigned a random VLAN ID based on MAC hashing algorithm. This helps to isolate broadcast packets and balance the load across different VLANs.
Before you start to manage EnGenius devices, you must first sign up for the service.
Registering EnGenius Cloud is similar to other web-based platforms and can be done either with a social media account (e.g., Google or Facebook) or by creating an account from scratch. You will need to provide your email address, company name, physical address, and phone number. Furthermore, you must determine the country in which your account will be hosted. That is, all relative device information, user configurations, and client statistics will be kept in the corresponding region of servers (Oregon for the US, Irland for the EU, Tokyo for JP, Mumbai for APAC except Japan). This enables EnGenius Cloud to protect customer data and comply with requirements like GDPR for customers within the European Union.
There are two ways for users to quickly pick up cameras for deeper inspection. Camera List can handle regular maintenance with plenty of information, while Camera Grid is the perfect way for video event investigation. Users can switch between the two modes for all cameras. Cameras can be shown here after being registered to the cloud and assigned to a network. To manage the cameras in a network, trigger the toolbar menu on the left-hand side: Manage > Cameras.
There’s a lot that EnGenius Cloud can do to customize a network to meet your specific needs. We’ll walk you through the most common settings here.
User can set for in-cam AI. There are 5 sensitivity levels for people and vehicles, respectively. By default, it is Medium. Lower sensitivity will have fewer video events.
By default, it is disabled. If enabled, people or vehicles could consume tokens to analyze their activities during the video frame. Note: Cloud AI can be enabled/disabled only if camera AI was enabled manually or by default. Cloud AI needs AI tokens to work. If AI tokens run out, video activity analysis will stop until AI tokens are recharged. Cloud AI events could depend on camera AI sensitivity since objects will be detected by camera AI and sent to cloud AI for advanced activity analysis.
These event alerts will send email/App notifications after you enable alerts on each event.
Event alert will also appear in the bell icon
Email Notification needs to be enabled; otherwise, alerts won't take effect.
Cross-line counting Alerts need to be added to the cross-line by clicking Edit line action
Region Counting Alert needs to be added to the cross-region by clicking the Edit Region action and assigning the people/vehicles that show up in any region.
This is the schedule that controls when to send the AI notification to the user, which will consume the AI Point as well. Camera AI handles detection, while other features like Camera AI Alerts, Cloud AI analysis, and Cloud AI Alerts follow the schedule. This allows for managing alert schedules and Cloud AI costs.
AI-Powered Search allows users to search by inputting natural and multiple languages in the free description form of a search bar, like they do on Google Search. Query is compared with camera metadata in the database across multiple cameras in an organization and ranking results in order. The user can explore result snapshots and play video clips of them
You can find the search bar from Manage > Cameras
Search results could be ranked in an order from top to bottom and left to right based on most relevant. Most relevant is the highest comparison score between the user query and camera metadata. Click on one of the result thumbnails to play a video clip of 15 seconds since the start time of the event. Clear search input to go back to camera list.
After users see the search result and want to get the alerts from the condition, you can add the condition to the SD Alert.
Click Manage > Switches to access this screen and double-click the organization/hierarchy view/network on the tree to change the scope.
The Switch List page lists all switches within your organization/hierarchy view/network, and allows you to choose each switch to view the port status, VLAN , STP and PoE.
The following describes the functions in this screen:
Move to: Select one or multiple switches and click to move the switches to another hierarchy view/network.
Remove From Networks: Select one or multiple switches and click to remove the switches from the current organization/hierarchy view/network.
Add From Inventory: Click this button to add switches from your existing inventory.
Detail: Click to display the individual switch details.
This allows you to clone SSID configuration which you created previously. So you can create Multiple SSID with same configuration easily.
Follow steps to clone SSID
Click Clone From
Select SSID to be cloned => Click apply in popup
3. Click Apply on tab bar to take effect
Bandwidth Limitation ensures that users do not consume more bandwidth than they should. We integrated bandwidth Limitation that enforces upload and download limits. Bandwidth Limitation can be applied per SSID or per user or both. When both SSID and Per Client bandwidth limit are set, that means when the total sum of client bandwidth is less than SSID bandwidth limit, per client can have a maximum of “per client bandwidth limit”. If the total sum is over the SSID limit, then all users will share the upper limit of SSID bandwidth.
Use this screen to configure maximum bandwidth.
Click Configure > SSID > Bandwidth Limit to access this screen.
Set the maximum download stream limit for traffic from the SSID or Per user .
Set the maximum upload stream limit for traffic from the SSID or Per user .
Captive Portal supports the way to authenticate via an externally hosted AD server. The option is available at Configure > SSID > Captive Portal > Active Directory.
Follow the steps below to configure your AD service.
1. Click Add a server to add a new AD server in the list.
2. Enter the IP address or domain name of your AD server in the Host field and the AD server listening port in the Port field.
3. For AD admin, enter the AD format: [email protected], and the password.
4. Click OK and then click Apply button.
Static routes are used to reach subnets that are not directly connected to or configured on the EnGenius Security Gateway, you can access this tab through Configure > Gateway > Interface > Static Route to add static routes to reach these subnets.
Enabled: Whether the EnGenius Gateway should use the route or not. Disable this setting if you wish to temporarily remove a route from the EnGenius Gateway without manually recreating it later.
Name: The name of the static route.
Destination: Use this option to enter the remote subnet that is reached via this static route (in CIDR notation).
Next-hop IP: IP address of the device (such as a router or layer 3 switches) that connects the EnGenius Gateway to the static route subnet.
EnGenius Cloud adopts an organization tree structure to let user define the scope of their managed networks. All device managing or monitoring functions can be applied to different scopes as laid out in the user's tree. That gives VAR or MSP users great flexibility in managing their networks.
The current organization tree structure consists of three levels, from largest to smallest:
Organization - A grouping of one or more hierarchies under the umbrella of a single license.
Hierarchy View - A cluster of networks, which may be geographically concentrated or spread out.
This page will show you the VPN status of the Gateway in relation to all other EnGenius Gateways or Non-EnGenius Gateways in your organization with site-to-site VPN enabled. You can access the VPN Status page by navigating to Manage > VPN Status.
If you are in the Organization scope, you could select the gateway to monitor the current VPN status in relation to other EnGenius Peers or NonEnGenius Peers by switching the tab
Under the EnGenius Peers tab, the following information is available
Gateway: The name of the EnGenius Gateway.
A network contains a list of devices and relevant information, such as configuration, SSID, radio settings, and firmware upgrade history. Each network contains a single configuration set for its devices, so if you have multiple configurations for devices, you can create a separate network to handle that.
Click Menu > Choose organization or hierarchy > Create network
When the actual Amp/Voltage exceeds the configured Voltage/Amp safe range, Cloud will log the events.
You can access this page from Manage > PDUs > Detail > Alerts
You can drag the bar to adjust the safe range and enable to logging the event that exceeds the configured voltage safe range.
Check the to see if any problem encountered. If Power LED keeps flashing for over 10 minutes, then there could be Cloud connection issues.
Use your mobile phone to scan if Default SSID of the AP found. (you have to be around the AP location) From the Default SSID, you can also identify which stage the AP is stuck on. See .
To troubleshoot the connection issue, you may login to Local page:
Network topology is a powerful tool to provide administrators a graphic overview of the logical network topology and the status of EnGenius devices.
Use this screen to view the topology of the Org/Network. Click Manage > Topology to access this screen and double-click the organization/hierarchy view/network on the tree to change the scope.
Learn which physical links in your network are most heavily-trafficked; simply hover over individual network links and devices to learn statistics about that connection’s negotiated speed, usage, and a number of directly connected clients using it in the past 5 minutes.
Captive Portal supports the way to authenticate with an externally hosted LDAP server. The option is available at Configure > SSID > Captive Portal > my LDAP server
Follow the steps below to configure the LDAP service:
1. Click Add a server to add a new LDAP server.
2. Enter the IP address or domain name of your LDAP server in the Host field and the LDAP listening port in the Port field.
3. For LDAP admin, enter the distinguished name of the administrative account to bind your LDAP server, for example, cn=admin,dc=example,dc=com, and the password.
4. Click OK and then click Apply
A hierarchy view is a group of networks and/or nested hierarchy views. It follows a tree-like structure much like folders on your computer's operating system.
You can create hierarchy views for a new organization or an existing organization, or even within an existing hierarchy view. Click Menu > Choose organization or hierarchy view > Add hierarchy view
AVExpress offers an end-to-end Quality of Service (QoS) solution specifically designed for crucial audio/video (AV) applications, including video conferencing, multi-media streaming, and gaming. It enables users to prioritize traffic based on its importance, ensuring that critical applications receive the necessary bandwidth and low latency for uninterrupted operation.
EnGenius AP will mark DSCP to those traffic to make sure it also gets the same level of priority through EnGenius Switches to reach end-to-end priority
you can access this page through Configure > SSID > Application Control
Application Aware: This allows users to see the application analysis on the client page . Disabling application awareness may improve WiFi performance.
AVXpress: Voice-related traffic will be prioritized as the highest level (Express), other traffic will be under General as normal applications, just like AVXpress is disabled. Fast is in the midst between Express
This setting allows you to configure Systems & Protocols in the network at once. This gives you to configure the System setting and apply it to whole Switches in the network. you can access this screen by Configure > Switch settings.
The settings are the same as you configure the individual switches , please refer to below page
This setting allows you to configure VLAN to all devices in the network at once . Table displays all VLANs have been configure in selected network .
Use this screen to add and delete VLANs for network.
Click Configure > VLAN Settings to access this screen.
The VLAN Settings page contains the following information :
VLAN ID : VLAN ID.
The Client VPN service uses IPsec VPN technology and can support VPN clients running on Windows10, macOS, iOS devices, and Android devices
To enable client VPN, choose Enabled from Configure > Gateway > Client VPN page.
The following client VPN options can be configured:
Hostname: This is the hostname of the EnGenius Gateway that client VPN users will use to connect to. If you have enabled DDNS service in your WAN settings, then the registered DDNS FQDN hostname is displayed which can be resolved to the Primary WAN public IP address of the EnGenius Security Gateway. If the DDNS service is not enabled or the DDNS update fails then the Primary WAN public IP address is displayed.
To configure an iOS device to connect to the client VPN, follow these steps:
Navigate to Settings > General > VPN & Device Management > Add VPN Configuration.
Type: Set to IPsec.
This page allows you to block clients in mac based on current SSID.
The following describes the functions on this screen:
Add : The entry for you to add the Mac address to be blocked.
Reset : Clean all the Block list .
Cause: AP does not have an Ethernet connection.
Solution: Check if the Ethernet cable is unplugged.
EnMGMTxxxx-No_IP
Cause: AP cannot get an IP address from the DHCP server. Solution: Check the AP's IP address configuration.
EnMGMTxxxx-IP_Conflict
Cause: AP’s IP address conflicts with another device’s IP in the same network.
Solution: Check the AP's IP address configuration.
EnMGMTxxxx-Gateway_ERR
Cause: AP is unable to connect to its default gateway.
Solution: Check the AP's IP address configuration and connectivity to its default gateway.
EnMGMTxxxx-Proxy_ERR
Cause: AP could not access Internet through an HTTP/HTTPS proxy.
Solution: Check the AP’s proxy configuration in Miscellaneous Settings.
EnMGMTxxxx-DNS_ERR
Cause: AP could not resolve the domain name from the DNS server.
Solution: Check the AP's IP address configuration.
EnMGMTxxxx-Cloud_ERR
Cause: Everything appears to work normally, but device is unable to connect to cloud server.
Solution: Check cloud server status with EnGenius.
EnMGMTxxxx-No_Cloud_Configure
Cause: AP’s S/N has not been added to any network.
Solution: Check whether the AP has been added in the inventory and has been added to a network.
EnMGMTxxxx-Cloud_Configured
Everything is working as it should!
EnMGMTxxxx
Cause: An AP has never connected to the EnGenius cloud or has been factory reset.
Use your client device (e.g., a laptop, mobile device, or tablet) to find the SSID: “EnMGMTxxxx” (xxxx is the last four digits of LAN MAC which can be found on the back of the device) and connect to it.
Enter the URL in web browser: http://EnGenius.local or the IP 192.168.1.1 to access the device’s user interface. You can review device status after logging into the AP with the default account/password ( default admin account/ password : admin/ admin.)
Issue: Cannot find Default SSID
1. Check for available wireless networks (Check if a known default SSID is being broadcast).
2. If a default SSID is being broadcast, connect your device to it.
3. If no known default SSIDs are present, set up a manual wireless network connection. For the SSID name, use 'EnMGMT', e.g. 'EnMGMTxxxx', where the x's are replaced with the last four digits of the LAN MAC address.
4. After connecting, open a web browser and connect to one of the local access page addresses.














VPN Client Subnet: The subnet that will be used for client VPN connections. This should be a private subnet that is not in use anywhere else in the network. The EnGenius Gateway will be the default gateway on this subnet and will route traffic to and from this subnet.
DNS server: The server's VPN clients will use to resolve DNS hostnames. Choose from Google Public DNS or specify custom DNS servers by IP address.
WINS server: If VPN clients should use WINS to resolve NetBIOS names, select Specify WINS Servers from the drop-down and enter the IP addresses of the desired WINS servers.
Pre-Shared Key: The shared secret that will be used to establish the client's VPN connection.
Authentication type: Use this option to authenticate Client VPN users with the local ESG VPN User database or select Custom RADIUS to use external RADIUS servers for authentication.
For detailed instructions on how to configure a client VPN connection on various client device platforms. please refer to the following instructions

Network - A set of network devices united by a single configuration set.
The organization tree definition is shown on the top left corner of the web GUI as follows:
Network: The Network to which the gateway is assigned.
WAN IP: The WAN IP of the remote gateway.
Subnet: The remote subnet network address behind the remote gateway that can be reached through Site to Site VPN.
Type: The type that is configured on the Configure > Gateway > Site to Site VPN
Usage: The amount of traffic to and from that EnGenius VPN peer.
Latency: Round-trip time latency between the EnGenius Gateway and the remote peers.
Uptime: This shows the time that the VPN tunnel has been active
If You are in the Network scope, it will display the gateway in the network to monitor the current VPN status in relation to other EnGenius Peers or NonEnGenius Peers.
On the non-EnGenius peer's tab, the following information is available
Gateway: Name of the EnGenius Gateway.
WAN IP: The WAN IP is configured for the non-EnGenius peer.
Subnet: The remote subnet network address behind the remote non-EnGenius gateway that can be reached through Site to Site VPN.
Users can drag & drop EnGenius Gateway and Non-EnGenius Gateway in the Organization to Google Maps and have a holistic view of the gateway deployed on google Maps and see the VPN topology. You can access this page Manage > VPN Status > Map
the color will show the latency of the VPN link to let the user has a quick view of the quality of each VPN link.

2. Enter a name for the network, select the country, time zone, and then click Create.
Network name, country, and timezone can be edited as needed. Follow the steps below to edit a network.
Choose network > Edit
If you no longer need a network that you previously created, you can delete it.
Follow these steps to delete a network.
Click Menu > Choose network > Delete
2. Popup is displayed. Click Confirm.
You can drag the bar to adjust the amp safe range and enable to logging the event that exceeds the configured Amp safe range.

Edit a organization if you need to update any its current settings (for example, if you want to change the Organization name, Country, TimeZone.)
Follow these steps to edit a Organization.
Click Menu > Find the Organization you want to edit > Edit
2. Update Network Settings as required
3. Click Apply
If you no longer need a Organization that you previously created, you can delete it.
Follow these steps to delete a organization
Click Menu > Find the Organization you want to edit > Delete
2. Popup is displayed and click Confirm
Show label: Click to display or hide the device name & HW status on each device.
HW status: Click to display or hide the POE utilization on each switch.
Redundant: Click to display or hide the redundant link .
Other Devices: Click to display the third party devices as well as EWS series devices. This requires switch PRO license and switch feature plan to PRO on switches.
Export : Click to download topology as PDF format .



Base DN: When you configure the LDAP server, you can set a Base DN. For example, If your domain name is example.com, you can use the Base DN dc=example,dc=com.
Login Attribute:
UID: (default ) use unique ID as the login attribute for user authentication
Email: use email format
Other text: Use user-defined string
You can edit the name of a hierarchy view name by clicking Menu > Choose hierarchy view > Edit
2. Change the Hierarchy View name and click Apply.
You can delete hierarchy views by clicking Menu > Choose hierarchy view and then clicking on the garbage icon.
After created Networks and associate devices, if the HV is changed, say, the Network originally belongs to North Region, and now become North-East Region, users have to change the HV and would like to move the Network under North-Region to North-East-Region. This allows users to "drag & drop" any Network to new HV under same Organization.
Open: Allows any client to associate with this network without any data encryption or authentication.
WPA2 PSK: Enter a pre-shared key of 8-64 case-sensitive characters to enable WPA2-PSK data encryption.
WPA2 Enterprise: Select Custom Radius to use an external Radius server or select the EnGenius Cloud Radius to use the EnGenius Cloud for 802.1X authentication.
OWE: When using hotspots in public, users are given better protection through the Wi-Fi Enhanced Open that provides unauthenticated encryption.
WPA3 Personal (SAE): This type features easier password selection for users to easily remember. It also feats a higher level of security wherein data stored and data traffic in the network will not be compromised even if the password was hacked and data was already transmitted. The upgrade also enabled the Simultaneous Authentication of Equals (SAE) which replaced the Pre-shared Keys (PSK) in WPA2-Personal.
WPA3/WPA2 Personal mixed: WPA2/WPA3 mixed mode allows for the coexistence of WPA2 and WPA3 clients on a common SSID. The passphrase for both WPA2 and WPA3 clients remains the same, the AP just advertises the different encryption cyphers available to be selected for use by the client. Clients choose which cypher to use for the wireless connection.
WPA3 Enterprise: This type was mainly built for tighter and consistent application of security protocols across networks of governments, establishments, enterprises, and financial institutions. Offering optional 192-bit minimum security, the WPA3 will make cryptographic tools better. Hence, better protection for sensitive data.
This QR code allows you to use your mobile device to connect to the specific SSID.
Mouse to click and draw a polygon by placing points on the camera’s screenshot.
Click each point sequentially to form the region.
Complete the region by connecting the last point back to the first point
You can adjust each point. If finished click apply.
Click on the starting point of the line within the camera's field of view.
Drag the line to the endpoint and click to place it. you can click the arrow icon to change the in/out direction.
Adjust the point location after you com
Click Apply
This will show on camera detail > Summary. Users can switch between “All Regions” and each region available. The numbers displayed on the charts represent the total people within the drawn region.
This will show on camera detail > summary. The user can switch between “All Lines” and each line available. The numbers displayed on the charts represent the total people In/Out traffic cross the drawn line.
NAME : VLAN name.
Voice VLAN : This shows if VLAN has been assigned to Voice VLAN or not.
SSID : the SSID that has been assigned the VLAN.
Click Add VLAN button.
Input VLAN ID and VLAN Name.
Click Apply to complete the settings.
Enter device details, device serial number, and device MAC address.
(You can input manually or upload in bulk via a CSV file.)
You can locate these values:
On the device’s label or in Gateway list on EnGenius Cloud
Go to Configure > Policies > Authentication > Add New > Device Auth.
Enter the required details, including: Realm (must match EnGenius Cloud settings).
Click Save to apply the policy.
Example: Realm = 123
Log in to your EnGenius Cloud account.
Navigate to Configure > Gateway > Security Service > CloudBrink.
Enable the CloudBrink service.
Enter the Realm value used in CloudBrink.
This ensures proper communication between platforms.
Example: Realm = 123
Go to Manage > Gateway Detail.
Check the CloudBrink status in Security Service.
Once CloudBrink status is RUNNING, it connected to CloudBrink edge node(s) successfully
Description: This can be anything you want to name this connection, for example, "Work VPN"
4. Server: Enter the hostname, the admin can find the hostname from Configure > Gateway> Client VPN
5. Account: Enter the username that the admin created on the Configure > Users > ESG VPN Users
6. Password: Enter the password that the admin created on the Configure > Users > ESG VPN Users
7. Secret: Enter the Pre-shared key that the admin find the key from Configure > Gateway> Client VPN
8. Click Done and Enable the VPN connection on the IOS Device.
3. Click Assign to Network.
Delete : Delete the list that you selected .
After you add the block list , remember to click Apply to take effect .
Once your account has been created, you can login to EnGenius Cloud in the following steps:
Open a web browser to https://cloud.engenius.ai/ . This will bring up the main login page.
2. Enter your EnGenius Cloud email address and password and click the Sign in button.
3. For EnGenius Partner who has account on EnGenius Partner Portal already, you can simply click on "E Partner" button, and EnGenius Partner Portal will pop up login page for you to use Single-Sign-On capability of Partner Portal to log on to EnGenius Cloud
4. For Google and Facebook users, you can also click on "Google" or "Facebook" button to use your account on Google and Facebook to log on to EnGenius Cloud
5. EnGenius Cloud will create a new default Organization and Network for every new account based on the email address as unique user identification. (note: If someone is invited to an Organization or Network, this account won't have default Organization and Network.) If you have multiple accounts created on EnGenius Cloud, EnGenius Cloud will merge your accounts based on the "email address" of the account. For example, if you have created a new account on EnGenius Cloud using the same email address as your google account, then you're able to login to this email account either through Google account authentication with Google account password, or through EnGenius Cloud Login with the password while you created the EnGenius Cloud account.
If you have problem getting the access point to Cloud, you can login to Local Access Page to do IP settings and diagnostics.
Use your client device (e.g., a laptop, mobile device, or tablet) to find the SSID: “EnMGMTxxxx” (xxxx is the last four digits of the MAC address, found on the back of the device) and connect to it.
Under your web browser, enter the URL http://EnGenius.local or the localhost IP address (192.168.1.1) to access the device’s user interface. You can review device status after logging into the AP with the default admin account/password (default account & password: admin/admin)
By default, EnGenius cloud access points (ECW series) are assigned an IP address dynamically by the DHCP server. If you encounter issues with IP address assignment, please double check that the IP settings include IP address, subnet mask, gateway, proxy, and management VLAN. If any issues still exist, you may change your IP assignment from "DHCP mode" to "Static IP" via the following procedure:
Every device's status page includes useful information about the status of the device, basic configuration options (such as setting a static IP), and other tools. The following section will explain the items available on the device status page.
ECW Access Points provide the following information and configuration options on their local status page:
Contains information regarding the device overview, EnGenius Cloud overview, and network connectivity information.
Provides information regarding the name, model, serial number, IP address, MAC address, and current firmware.
Provides information about the Cloud registration status, date of registration, and time of last update.
Provides connectivity information to local network, Internet, and EnGenius Cloud.
Provides settings for IPv4 / IPv6 address, management VLAN, firmware upgrade, and other miscellaneous configuration items (such as HTTP/HTTPS Proxy). Users can also reboot the device or reset the device to factory default settings from here.
PDLG is a function that will automatically reboot PD devices when PoE switch found it was not responding. Which minimizes the downtime of network services and reduces admin effort via automatic processes.
In PDLG force ping mode, user have to set PD device IP manually. By keep pinging PDs, switch knows if PD is still alive or has to be rebooted.
PDLG also support auto mode which allows switch collecting PD information/status through LLDP preventing any PD IP changes under DHCP environment.
By fine tuning the reboot profiles, PDLG can correctly detects/reboot various PDs since every PD devices may have different response or bootup time.
ACLG is one of the option in PDLG auto mode. By enable ACLG, switch also considers Onvif discovery result to verify if the connected PD is surveillance device or not. Once switch make sure it is a surveillance device, it applies a ACLG reboot profile to corresponding port automatically.
Specified IP: Setting specified IP on a specific port.
Ping Interval: Setting ping IP interval on a specific port.
Ping Max Count: Setting ping max count on a specific port.
The default value of PDLG & ACLG is from the network wide profile settings
You can click lock icon to override the settings
This allows you to view and configure PoE schedules that can be applied to the ports. Below screens display the existing schedules visually. Click Manage > Switch lists > detail > PoE scheduling to access this screen
Select the ports to be set the PoE scheduling then click Edit
2. Enable scheduling and then customize the PoE on or Off by dragging the bar. This behavior is the same when you configure the SSID scheduling.
3. If you want to do the PoE reset, you can simply click PoE rest and then drag the icon to the specific time.
4. Click Apply.
Port Mirroring allows you to copy packets on one or more ports to a mirroring destination port. You can attach a monitoring device to the mirroring destination port to view details about the packets passing through the copied ports. This is useful for network monitoring and troubleshooting purposes. The feature is available is at Manage > Switch < Details > Mirror
The following describe the labels on this screen :
Session id : A number identifying the mirror session. Switch supports up to 3 mirror sessions.
Session State : Select whether to enable or disable port mirroring.
Destination Port : The port which all mirrored data is sent to .
Ingress : indicates that only data being received will be mirrored.
Egress : indicates that only data being sent will be mirrored
Click the edit icon towards the right .
Enable the Session state.
Select the Destination port
Select the Ingress and Egress port
There are four types of port that you configured .
Port was assigned to a destination port . Port was assigned only data being sent will be mirrored . Port was assigned only data being received will be mirrored . Port was assigned both directions of data are being mirrored to the destination port.
Floor plans allow you to simulate the heatmap. This article will discuss how to upload custom floor plans, pin them on the map, and place devices within these floor plans.
Before uploading floor plans, a building must be created to contain them (see Managing Devices > Device Map Location in the user manual).
To upload a custom floor plan/map:
1. Navigate to Manage > Map & Floor plans.
2. Click Building and click Add.
3. Enter a name and then click Create.
4. Find the building you have just created in the building list and click the picture icon.
5. Enter a name and upload the floor plan, then click Apply.
If you no longer use a floor plan that you previously imported, you can delete it.
Follow these steps to delete a floor plan:
Find the building you created in the building list.
When the floor plan appears, hover over it and click Delete.
Virtual AP” is now available for users to add virtual AP together with “physical AP”, so users can simulate the heat map if he adds more AP to increase the coverage
Add Virtual AP and choose units of models to add
The Tool icon for users to modify the tx power and channel for heat map simulation
Drag the physical AP to Virtual AP (model needs to be the same) then physical AP could use the Virtual AP configuration.
When drawing the walls, users used to draw the line one by one by click “start” and “end” for straight lines, now with the “Polyline” option available, users can simply click on the turning point to draw lines quicker.
PBR (Policy-Based Routing) enables precise control over network traffic by defining routing policies based on criteria like source/destination IP addresses or layer 4 port numbers. This capability resolves challenges related to inefficient network resource management, providing organizations with greater flexibility and control over traffic routing and optimization.
By defining routing policies, you can route traffic over preferred network paths, prioritize certain types of traffic, or balance traffic across multiple links for load balancing and optimization purposes.
PBR can be used to implement Quality of Service (QoS) policies to prioritize critical traffic types, such as voice or video communications, over less time-sensitive traffic.
You can access this page through Configure > Gateway > Interface > Policy Route
You can create policy-based routing rules to direct specific applications to different WAN interfaces without specifying IP addresses or port ranges
Optimized Traffic Management: Direct critical applications to a primary WAN while routing less important traffic to a secondary WAN
Enhanced Network Performance: Improve network efficiency by balancing load between WAN interfaces based on application
Simplified Rule Management: No need to update routing rules for changing IP addresses or port ranges
Enterprises are increasingly relying on SaaS services such as Gmail, Windows 365, and CRM tools like Salesforce.com, making these services more critical than other internet traffic that it is better to separate the traffic from others. In this scenario, users can strategize as follows:
Designate WAN1 as the primary WAN and WAN2 as the failover WAN, with most traffic routed through WAN1
Route business-critical SaaS traffic, such as Gmail, Windows 365, and Salesforce.com, through WAN2
The figure below illustrates layer 7 policy-based routing rules for directing entire categories and specific applications within a category to different WAN interfaces
Go to Configure > Gateway > Interfaces > Policy Routes > Layer 7> Add Rule
A captive portal can intercept network traffic until a user authenticates his/her connection, usually through a specifically designated login page.
Click Configure > SSID > Captive Portal to access this screen.
Click-through: Users must view and acknowledge your splash page before being allowed on the network.
EnGenius Authentication: Users must enter a username and password before being allowed on the network. You could edit user settings through Configure > Cloud RADIUS User.
Custom RADIUS: Enter the host (IP address of your RADIUS server, reachable from the access points), port (UDP port the RADIUS server listens on for access requests, 1812 by default), and secret (RADIUS client shared secret). Optionally, the Accounting Server can be enabled on an SSID that's using WPA2-Enterprise with RADIUS authentication.
Voucher Service: Edit the access plan for guests for the front desk manager.
Google LDAP:
Active directory:
Configure the URL to which users will be redirected after successful login.
Redirect to the original URL: Select this option to cache the initial website from the client during the authentication process and then forward it to the originally targeted web server after the user successfully authenticates.
Redirect users to a new URL: Select this option to redirect users to a pre-designated URL after the user successfully authenticates.
Session Timeout: Specify a time limit after which users will be disconnected and required to log in again.
Idle Timeout: Specify a time limit for an idle client after which users will be disconnected and required to log in again.
Walled Garden: This option allows users to define network destinations that users can access before authenticating. For example, your company's website.
HTTPS Login: This option allows users to log in through HTTPS. When you enable it, your password is encrypted, so others could not retrieve your information.
When setting up an enterprise wireless network, it is common to configure WPA2-PSK authentication in order to onboard different users on to the wireless network. However, IT administrators may still encounter some drawbacks with this method of authentication when they need to use different PSKs in order to assign different VLANs. MyPSK allows a network administrator to use multiple PSKs and assigned different VLANs per SSID.
Before Configuring the MyPSK Users, please make sure you have chosen the Cloud myPSK user From Configure > SSID > Wireless > Security Type > WPA2-MyPSK
You can access this screen from Configure > EnGenius.Auth > MyPSK Users > Add Users
The following describes the labels on the popup.
Auto-Generated: Click the checkbox and then input the number of the users you want to create. Auto-Generated Users are limited to 50 per time.
PSK: Input the password for the user to log in, Auto-Generated Users will have PSK automatically.
VLAN: By SSID means the user is assigned the VLAN from the SSID which you choose to authorize. If you see the VLAN you wanted is not displayed, you could add the VLAN from Configure > VLAN Settings, then you could select from the dropdown list.
Allowed MAC: Only the User with this Mac Address could access the SSID, leave it blank if you don't want to restrict it.
Expired Date: Default is Permanent, click the checkbox to choose the expired date
User note: Add note to map “the user” to the “PSK” to “identify” the person
SSID Authorized: The SSIDs you want users to access
1.Click the number on the Authorized SSIDs or each PSK
2. Allows you to edit the details of each user.
L2 isolation is a feature to prevent wireless client from communicating with any other devices in the network except gateway. With this feature enabled, not only clients associating with the same SSID cannot communicate with each other (this is so called client isolation conventionally) but also clients cannot access other devices in the same LAN. Another exception is that wired devices added to VIP list are still accessible.
This feature is useful for guest SSID, enhancing security by limiting potential attacks and threats between clients on the wireless network.
Dual band operation with Band Steering detects clients capable of dual band operation and steers them to another frequency which leaves the more crowded band available for communication. This helps improve the end-user experience by reducing channel utilization, especially in high-density environments. Band Steering is configured on a per-SSID basis.
This value defines the minimum RSSI required for dual-band wireless clients to associate to 5G band. If the client's RSSI drops below this threshold, it is only allowed to connect to 2.4G band. The recommended value is -60~-80.
BCMC suppression is a feature to drop all the broadcast and multicast frames on a VLAN except for ARP, DHCP, IPv6 router advertisement, and IPv6 neighbor solicitation.
Broadcast-Multicast traffic from APs, remote APs, or distributions terminating on the same VLAN floods all VLAN member ports. This causes critical bandwidth wastage, especially when the APs are connected to an L3 cloud where the available bandwidth is limited or expensive. Suppressing the VLAN broadcast-multicast traffic to prevent flooding can result in loss of client connectivity.
To effectively prevent flooding of broadcast-multicast traffic on all VLAN member ports, use BCMC Suppression to ensure controlled flooding of broadcast-multicast traffic without compromising the client connectivity. This option is for the controlled flooding of broadcast-multicast traffic and is enabled by default.
Enterprise network with over 1000 active wired or wireless clients in different VLANs.
Campus network with over 1000 active wired or wireless clients in different VLANs.
This allows you to run the diagnostic tests that can help the Network administrator to troubleshoot.
Under the PDU detail page > you can easily see the “Diag Tools” icon
or Under Manage > PDUs > Diag
Click it and then the Full-screen tools are displayed, So you can use them.
Diag Tools are all “real-time”
PDU diagnostic tools include (1) Activity: CPU/Memory/Power/Current (2) Ping (3) Traceroute
Ping: We put 3 default servers for users to check the latency change. User can also define their own server for the ping test.
Traceroute: By default, we set the destination site to Google for the traceroute, and max hop is set to 8, which can be changed by the user. Traceroute allows users to know “the path” from the PDU to the destination and will list every router/gateway (hop) and its latency, so if the destination is unreachable, then there must be some setting issue on the router/gateway; and from the latency of each hop, the user will know the “slow uplink” is caused by which router/gateway. When the latency is over 10ms, the color will change to yellow, and if > 40ms, the color will change to red. These color variations help you quickly identify potential performance issues in the network path. To conduct a trace, click the Trace icon.
This screen allows you to locate a device on the world map to show the relationship between the space and EnGenius Devices. Maps provide a visualization for buildings and access points.
A building means a group of floor plans. You can create a new building with the + button.
After you create a building, you can drag it to the map. Single-click on the building icon and a hyperlink will appear to allow you to edit floor plans.
Click access point list or buildings list.
Enter the street address in the address field.
Drag the access point/building onto the map.
There are a number of ways to navigate through the map display.
Single Click: If the user single-clicks on the focus icon on the access point or building lists, it will auto-locate the same item in the map.
Double Click: If the user double-clicks on the building icon in the access point list, the UI will auto-navigate to the floor plans of that building.
Before you begin configuring a captive portal, you need to create a SSID. Navigate to Configure > SSID (If you can't click configure, please make sure you are on network scope).
2. Select one of the SSIDs from the list. If one is not available, please click Add SSID to create one.
3. Navigate to the captive portal and click Enabled and then select the authentication type.
4. Click Apply.
1. Go to Setting > Connection & Sharing
2. Click VPN
3. Click add VPN
4. Set Office Profile Name, Security type, Server address IP, IPsec pre-share key, Username, and Password, and Click the Save button.
5. Click Office VPN profile to start a connection, When the VPN client connects to the VPN server, it will show the key icon on the top bar status, and the Profile name will show connected.
6. When you want to disconnect the VPN connection, please click the toggle button to disconnect VPN.
This allows you to configure the EnGenius Gateway VPN user to use the Client VPN. You can access this page from Configure > EnGenius Auth. > ESG VPN Users
The following describes the labels on this screen:
Name: Shows the descriptive name of the user account.
Created by: This User is created by whom.
Created time: When the user has been created.
Description: the remark that you can add the note on this user.
This helps “group configure PDUs” in the network. The PDU Template feature helps users apply the same outlet configuration to all PDUs with the same models in the network to save time on configuration one by one.
you can access this screen by going to Configure > PDUs > Template
You can create any template by model type and then click on “Edit” on the template to configure detail; the setting is similar to PDU detail page settings.
Click the "Apply to all" button to deploy template settings across all PDUs of the same model within the network.
802.11r is a standards-based fast roaming technology that is leveraged when using a secure SSID (WPA2-PSK & WPA2-Enterprise). This option improves client device roaming by reducing the handoff delay in situations where client devices roam from one access point to another. 802.11r is disabled by default on EnGenius Cloud.
This feature can be enabled from the Configure > Access Point > SSID page under Network Scope.
If this option cannot be enabled, please go to Wireless > Security Type to select WPA2 PSK/ WPA2 Enterprise /WPA3 Personal (SAE) /WPA3-Personal/WPA2-PSK mixed in advance.
802.11w is enabled when Security Type is not Open. 802.11w enables Protected Management Frames (PMF) for management frames such as authentication, de-authentication, association, disassociation, beacon, and probe traffic. This enables APs to help prevent rogue devices from spoofing management frames from APs. Enable 802.11w will allow APs to begin utilizing Protected Management Frames for any clients that support 802.11w.
Live view, playback, and smart motion search are combined into one panel to reduce switching operations between each other. Normally, users spend time searching for videos on the timeline. Here smart Motion search makes it easy and reduces the number of times to play back and forward on record track
you can access Video Playback from Monitor > Camera > Videos
If Outlet AutoReboot is Enabled, PDU will perform a power cycle for outlets that are ON when communication with the assigned website/IP address is lost.
You can access this page from Manage > PDUs > Detail > AutoReboot
Link aggregation groups multiple ports together in parallel to act as a single logical link. Aggregation-enabled devices treat all physical links (ports) in an aggregation group entirely as a single logical link (port). Member ports in an aggregation group share egress/ingress traffic load, delivering a bandwidth that is multiple of a single physical link. The feature is available is at Manage > Switch < Details > Link Aggregation
To Configure trunk , you must select aggregation type . Select from the following options:
This allows you to run the diagnostic tests that can help the Network administrator to troubleshoot.
Under AP detail page > you can easily see the “Diag Tools” icon
Under Manage > Access Points > Diag
So the Full-screen tools are displayed, So you can use them.
Diag Tools are all “real-time”
This allows you to run the diagnostic tests that can help the Network administrator to troubleshoot.
Under switch detail page > you can easily see the “Diag Tools” icon
Under Manage > Switches > Diag
So the Full-screen tools are displayed, So you can use them.
EnGenius Cloud AP can leverage Microsoft Azure AD to provide a highly secure authentication process for WPA2/WPA3-Enterprise or Captive Portal. The benefit of using Azure AD is that users may integrate WPA2/WPA3-Enterprise or Captive Portal with Azure AD to identify the specified domain/credentials quickly and account Emails for authentication management.
There are two ways to enable Azure AD to authenticate wireless users with EnGenius Cloud.
Enable Security Type WPA2/WPA3-Enterprise with Azure AD.
Enable Captive Portal for user authentication with Azure AD.
This guide is intended to help you set up your network to generate and accept vouchers. With vouchers, you control access on a per-user basis by generating guest passes you can provide to users.
Vouchers can be set to specific time increments and are ideal for hotels, coffee shops, apartments, etc. where you want to limit network access to users for a specific period of time.
Enable the voucher service by clicking Configure > SSID > Captive portal > Voucher Service.
The Cloud RADIUS User is used when you select the EnGenius authentication from Configure > SSID > Captive portal > Authenticated type
or SSID > Wireless > Security Type > WPA2/3Enterprise > EnGenius Cloud RADIUS
Double-click one of the networks on Org-Trees > Configure > Users > Cloud Users to access this screen to view and manage user accounts authenticated using EnGenius Cloud RADIUS.
The following describes the labels on this screen:
Many MSPs or SI would like to be able to “group configure port settings” in the Network. The Switch Template feature helps users to apply the same port configuration to all switches with the same models in the Network to save the time of configuration one by one.
you can access this screen by Configure > Switch Settings > Template
You can create any template by model type and then click on “Edit” on the template to configure detail; the setting is similar to switch detail page settings.
Apply to All will apply the Switch Template to all devices of the same model in the Network.
For network security, the hotels often set up the room network as a Guest Network with L2 isolation enabled to prevent guests from accessing each other's devices. Under the Guest Network, the guests will be blocked from casting multimedia of mobile devices onto the room TV, which causes inconvenience and a poor stay experience for the guests. The newly released EnGenius SmartCasting feature provides smooth, fast setup and streaming on Guest Networks for media sticks, game consoles, and other devices for an exceptional, personalized entertainment experience. This Intelligent feature of EnGenius Cloud is different from the simple technology of simply casting to a Chromecast and AppleTV.
Create a new service and select VPN connection with Cisco IPSec
2. Enter server address and account/password
3. Enter the pre-shared key
Hotspot 2.0, also known as Passpoint, is a service provider feature that assists with carrier offloading. Hotspot 2.0 SSIDs include additional 802.11u information that supported client devices can use to determine if they are able to join the network automatically.
Operation Name : Input the displayed Hotspot 2.0 network name
Venue Name / Type : Input the Venue Name .
Venue Type : Specify the venue groups to be advertised in the IEs from APs associated with this hotspot profile.
Network Type : Access the network type in beacon.
Domain List : This information element specifies the APs domain name.
Roaming Consortium List : This information element contains information identifying the network and service provider, whose security credentials can be used to authenticate with the AP transmitting this element. Input the Roaming Consortium Organization Identifier
PD BootUp Time: Setting Powered Device boot-up time on a specific port.
Reboot Max retry count : Setting the max number of reboot
LLDP/ACLG Expiry pending time: Settings the corresponding LLDP expiry pending time.







Email: Shows the email of the user account.
Authorized SSID: This shows the SSID numbers that the user has authorized.
Create Date: This shows the date and time that the user was created.
Status: This shows whether the user has been blocked or not.
The following describes the functions on this screen:
Add User: Add users and authorize users to SSIDs.
Authorize: This allows you to authorize users to SSIDs.
Delete: Delete users.
Block: Block users.
Unblock: Unblock users.




3GPP Cellular Network Info: This information element defines information for a 3GPP Cellular Network for hotspots that have roaming relationships with cellular operators. Input the mobile country code and mobile network code.
NAI Realm : This information element identifies and describes a NAI realm accessible using the AP and the method that this NAI realm uses for authentication. Input the Network Access Identifier Realm Names.































Click Apply
In the SSID => Wireless => WPA2 myPSK , there is an option "Auth with External RADIUS Server, which is supported with AP v1.X.25 firmware or above. Available models : (ECW220/230/260)
Pick a specific day and time on the calendar.
Scroll on record track and then mouse up and down to the appropriate duration scale where event stamps on the timeline are clear.
Click pre- or next-events on the timeline, or mouse over the timeline to pop up an event snapshot and click on the timestamp to the time point.
Once abnormality is found, click pre- or next frame to locate a clear moment and take a snapshot or export a video clip.
This allows you to identify people and vehicles within the camera's field of view and quickly find relevant events.
You can click the smart motion search on the top-right corner at the beginning.
Set an interest region on video. Results are shown on paging, sorting from latest to past.
Check the snapshot or scroll down to the next page of results. Once an abnormality was found, click on the snapshot to playback the video clip on the timeline. Each time duration can have multiple search result , you can click right or left arrow icon to find it.
Once you can't find the results you want, you can click the filter icon to search based on the time duration.
Click pre- or next frame to locate a clear moment and take a snapshot or export a video clip.
This allows you to identify people within the camera's field of view and quickly find relevant events.
The details steps are the same when you do the motion search, but change to the People tab.
This allows you to identify vehicles within the camera's field of view and quickly find relevant events.
The details steps are the same when you do the motion search, but change to the Vehicle tab.
FullScreen: click to have fullscreen of the videos.
Camera detail: Go to the camera detail page to adjust camera settings.
Share URL: Anyone who has the URL can access it without authentication. The video is not autoplay to be able to have audio when playing. It is easy to share an abnormal event with a person who has no EeGenius account, like police.
Audio On/Off: Enable/Disable microphone of camera to pick up remote audio.
Export Video: Trim video from start time to end time on timeline
Snapshot: Directly have a snapshot at that moment when you click the button.
Previous/Next Event: Quickly navigate through recorded events in the camera's playback timeline.
Stop at previous/next frame: Precisely navigate through recorded footage frame by frame. This is especially useful for detailed analysis or capturing specific moments in the footage.
Play/pause video: click to switch to play or stop video and adjust the volume.
Play speed: This allows you to adjust the play speed. If you play at higher speed, you will get more footage frame from the cameras and double more throughputs.
Digital Zoom: Adjust the zoom level and focus on specific areas of the camera's view using the mouse.
Scroll Up: Zoom in to view details more closely.
Scroll Down: Zoom out to expand the field of view.
Click and Drag: After zooming in, click on the screen and drag to adjust the visible area within the zoomed-in frame.
Adjust the timeline duration: Allows you to change the time line duration for the video time bar.
Live icon: click to go to live view instantly.
Calendar: Click to search the video footage at a specific day and time directly.

To configure the outlet reboot, complete the following steps:
Select the outlet from the list and click Edit.
Enable the AutoReboot function.
Specify the condition that prompts an auto reboot and enter the host details.
Click OK and then click Apply.
This allows you to configure the Autoreboot timeout settings.
AutoReboot Ping interval: the time period that will ping to the connected devices.
AutoReboot Delay Time: Sets the amount of time before AutoReboot resumes pinging once an auto reboot has been performed.
AutoReboot Attempts: Amount of auto-reboots to attempt when communication with a website/IP address is lost.
The Reset action will appear when the outlet has reached the maximum number of auto-reboot attempts. The AutoReboot feature uses Ping to check if devices connected to its outlets are working properly. If the "Pinged Host" encounters ongoing network issues, the PDU automatically reboots the related outlet to resolve the problem. This is particularly useful in unmanned locations, as it minimizes downtime, reduces the need for manual intervention, and ensures the stable operation of critical infrastructure.
Currently, the releated outlet will STOP the AutoReboot mechanism once the maximum number of AutoReboot attempts has been reached.
However, after the administrator resolves the issue with the abnormal device connected to the outlet, they may not always be aware that the AutoReboot function has stopped.
To address this challenge, a new feature "Reset" Action is introduced to allow the AutoReboot mechanism to be restarted directly from the cloud interface.
When an outlet reaches the maximum reboot attempts, EnGenius Cloud will show a "Reset" button in the "TIMEOUT SETTINGS" section of the AutoReboot page, located under MANAGE > PDU > PDU List > Click Specific PDU > Detail, prompting the user to take action.
After clicking "Reset" to allow the AutoReboot mechanism to be restarted. It requires firmware: v1.0.20 or later.

LACP: LACP is a dynamic protocol which helps to automate the configuration and maintenance of LAG’s. The main purpose of LACP is to automatically configure individual links to an aggregate bundle, while adding new links and helping to recover from link failures if the need arises. LACP can monitor to verify if all the links are connected to the authorized group. LACP is a standard in computer networking, hence LACP should be enabled on the Switch's trunk ports initially in order for both the participating Switches/devices that support the standard to use it.
Static: Static configuration is used when connecting to a switch that doesn't support LACP.
Disable : Disable the trunk that you configured previously.
Then select the Member Ports to add into the trunk group. There are two ways to select the ports
Click on the port picker to select multiple ports.
2. Click Pencil icon to input port numbers
After you complete the trunk settings , remember to click Apply to take effect .
AP diagnostic tools includes (1) Activity: CPU/Memory/Throughput/Channel Utilization(2) Speed test / Ping (3) traceroute (4) All channel utilization (5) Live Clients + (6) Spectrum Analyzer
Except Spectrum Analyzer is for “S” models only, (1)-(5) are all available for all models
Activity: The info is as now and we add “non-WiFi” channel utilization % to let users know how much of the total channel utilization rate is from non-WiFi, so users can know if the interfering is from other AP or the environment of the channel is dirty and got high white noise.
For the Speed test, users can choose one from the “Test Server” list (detected by AP) and do a speed test, so when users have an issue on “slow connectivity” issue, the admin can check if it’s due to “Slow uplink” of AP or due to dirty WiFi between client and AP.
Ping: We put 3 default servers for users to check the latency change. User can also define their own server for the ping test.
Traceroute: By default, we set the destination site to Google for the traceroute, and max hop is set to 8, which can be changed by the user. Traceroute allows user to know “the path” from the AP to the destination and will list every router/gateway (hop) and its latency, so if the destination is unreachable, then there must be some setting issue on router/gateway; and from the latency of each hop, the user will know the “slow uplink” is caused by which router/gateway. When the latency is over 10ms, the color will change to yellow, and if > 40ms, the color will change to red.
All channel utilization: This is a useful tool that user can easily see how dirty each channel is at a glance, and decide if he wants to change the channel of the AP manually. “Green” is “WiFi” traffic and “Orange” is “non-WiFi” interfering. By mouse-over, you can see the details of how much the % of WiFi and non-WiFi.
For the spectrum analysis tool (spectrogram or waterfall graph), we provide a rolling timeline view of signal strengths measured. The upper part shows the signal strength (RSSI) detected and the color indicates how many sources have been detected. The Lower part is the timeline view to let users know that, for example, channel 8 is dirtier than others, which might not be able to show from glance view of all channel utilization at the time, because the interfering source might not emit continuously but in high frequency.
In the Live clients, you can monitor the clients that are connected to specific AP. You can use it when the AP feature plan is PRO.
3. Hardware version on ECW AP
The serial number for an ECW AP can also be found on the sticker on the back on the unit (check where you plug in the Ethernet cords into the ECW AP)
Below is an example of the sticker on the back on an ECW220 AP.
As you can see the sticker on the back of the AP has the MAC address of the AP as well. It has the following items:
1.Model of AP
2.Serial number of ECW AP (This string of information that is added in the Cloud GUI)
You can also find the serial number of the ECW AP In the GUI of the ECW AP, when you login into the unit.
Highlighted below is the information needed to add the AP to the Cloud GUI, if the information is obtained via login to the ECW AP locally in the web GUI.
1. Model of the AP
2. Serial Number of ECW AP (This string of information that is added in the Cloud GUI)
3. Firmware version the AP is currently running
Below is the sticker that is on the box of the ECS switch
Model of the ECS switch
2.Serial Number of ECW AP (This string of information that is added in the Gloud GUI)
3. Hardware version of the ECS switch
4.Firmware version that the switch came shipped with
Below is the information you find when you login to the ECS switch locally and go to System > Summary from the left hand column.
Model of ECS Switch
2. Serial Number of ECW AP (This string of information that is added in the Gloud GUI)
3.Firmware version the switch is currently running
Overall port status view - It’s a good way to let users see all ports throughput at a glance
The bar indicates the throughput of the port and the color of the bar indicates the speed of the port.
CRC error
This is an important indication to see if anything is wrong with the transmission including the cable issues. The red square indicates there are CRC errors found. Users can mouse over to the port and see more details of throughput and CRC error count.
This is the real-time client list of the Switch or the content of the forwarding table. Users can refresh the table by clicking the refresh button
Cable diag helps to check the Cable status of selected ports. (It can be multiple selections) and will show the possible distance of breaking points.
In order to send packets on LAN, network devices need to know the IP and MAC address of the hosts they intend to communicate with. Address Resolution Protocol provides the mechanism to determine the MAC address associated with an IP address. These IP to MAC bindings are stored in each switch's ARP cache.
The packet capture utility can be used to observe live network traffic passed by EnGenius Switches. Since captures provide a live snapshot of traffic on the network, they can be immensely helpful in diagnosing and troubleshooting network issues. This article outlines how to remotely take a packet capture in Diag tools.
Choose ports to capture packets > input Duration in sec > click on “Capture”, then the Switch will collect the packets and download them with the .pcap file
2. Download Wireshark or other packet analysis tools to open up the .pcap file



Go to Configure > SSID and select a specific SSID name from the list
From the Wireless tab, select WPA2 /3 Enterprise for Security Type
Select Azure AD for user authentication
Enter the configuration (Host, Port, Account, and Password) for the Azure AD.
Host: IP address or domain name of your Azure AD
Port: Azure AD listening port
Username: Azure admin account ([email protected] )
Password: Azure admin password
Base DN: dc=example,dc=com (Corresponding to the domain service, such as example.com)
Click the Apply button to save SSID configurations.
Go to Configure > SSID and select a specific SSID name from the list.
Enable Captive Portal from the Captive Portal tab.
Select Azure AD for Authentication Type
Enter the configuration (Host, Port, Account, and Password) for the Azure AD.
Host: IP address or domain name of your Azure AD
Port: Azure AD listening port
Username: Azure admin account ([email protected] )
Password: Azure admin password
Base DN: dc=example,dc=com (Corresponding to the domain service, such as example.com)
Click the Apply button to save SSID configurations.
Note: Authentication with Active Directory is a feature in Pro Plan, and it requires a PRO license to enable it.
Note
Please make sure that the Security Type at Configure > SSID > Association has been configured as open or WPA2 PSK before trying to enable Voucher Service. Since the Voucher Service is capable of generating user/password randomly, it can not work with a dedicated WPA2 Enterprise authentication server.
Please make sure you add the Front desk account to the EnGenius Cloud by adding user front-desk privilege before you click to send a notification to the Front desk manager.
Remember to click on the Apply button at the top-right corner to confirm your change on SSID settings.
For each enabled voucher service, a dedicated Management URL is created. Any team members who have permissions of Front-desk Manager or Administrator can log in that specific URL and manage Voucher Users there.
In addition, you can create different Plans for voucher user to identify how long a voucher user can access the network (Access Time) and how many simultaneous login are allowed for that user (Simultaneous Login).
The plan start time is an option that defines the plan of voucher service is activated when an account is created or after the account's first login.
The first page after you login the Management URL of Voucher Service allows you to generate guest account/password with different manners:
A network Administrator or Front-desk Manager can firstly select a access plan and then select to generate account/password of voucher user automatically or manually. Auto Generation allows you to generate Guest pass in batch , you can fill in the number of the Guest Pass you want to create.
Click on the User Management Button in the toolbar.
A Guest Management Page is performed to list all generated voucher user. You can edit the properties of a voucher user by clicking the user_id of that user or pick the users in that list to delete.
In the Guest Management Page, you can also select the users and click on the print button to print the voucher info for end-user. This feature allows you to print voucher users in batch.
Note
The uplink port will not be overridden by the template to prevent losing connection.
The Uplink port couldn't be the Mirror destination port
PoE on the ports should be enabled when the ports are configured with the PoE schedule on the devices.
For Hospitality or other network environments, the network administrator will purchase the same model of the switch and define the same port function, say port 1 for TV for VLAN1, port 2 for IP phone for VLAN 10, and other ports for VLAN 11-50.., with the switch template created and import the VLAN settings, it will apply to all switches of the same model, which ease the job of switch configuration one by one
This will export the current VLAN JSON file and allows you to edit locally.
You can click the example hyperlink to download the JSON file
and then adjust the VLAN settings locally
then click JSON file upload to import your custom JSON file.
So you can import VLAN settings at a time instead use the current Web GUI to edit one by one
You can apply the switch template to the same model of the switches from
Manage > Switch List > choose the Switches to be applied > Choose Apply Template
Create the SmartCasting SSID in EnGenius Cloud, and the SmartCasting SSID will have all casting devices under this SSID and allow them to cast to the device.
The SSID of SmartCasting can be accessed with a predefined URL, and this URL will be available for guests via a QR code.
By scanning the QR code, the hotel guests will be able to quickly cast the media on mobile devices to the room TV screen.
1. Go to CONFIGURE>SSID.
2. Create a new SSID for casting devices > choose the SSID type to “SmartCast” > Add casting devices
3. Connect all casting devices to the SSID. 4. Auto or manually add casting devices.
Auto: Connect your casting devices to the SSID first > The Auto mode will scan the casting devices connecting to the SSID.
Manual: Manually add the casting devices by their MAC address.
Download the “QR code” of each casting device and insert it into the backdrop of the casting device for guests to scan the code showing on the TV or print the QR code out and place it in each room.
The TV icon will display near the SSID name, which means this SSID has enabled SmartCasting.

4. Connect to VPN server



2. Enable scheduling and customize the outlet on or Off by dragging the bar. This behavior is the same when you configure the SSID/ PoE scheduling.
Available: the outlet will be powered on according to the scheduled criteria.
Unavailable: the outlet will be powered off according to the scheduled criteria.
3. If you want to do the outlet reset, click outlet reset and then drag the icon to the specific time.
Outlet reset: Specify when to temporarily disable and enable the outlet when the outlet's availability is set to Available.
4. Click Apply.
Provide a more flexible schedule configuration, allowing users to adjust the specific days of the week for each outlet according to environmental needs to set up to three available time slots.
1. Navigate to MANAGE > PDUs > Schedule to select the specific outlet and then click the Edit Button.
2. Use the parameters of the "Time Slider" to adjust the availability of time slots for each day.
Available firmware: PDU firmware v1.0.5 or later version.

For each Gateway, EnGenius Cloud collects and aggregates lots of data reported by the Gateway periodically. Sophisticated graphs and tables are available on the gateway detail page to ease the monitoring and tracking of a gateway. To get all the details, on the Gateway page, hover your mouse cursor on the row of Gateway you are interested in. A Detail button is shown click on it to get into the Gateway detail page.
This will display the WAN Info that you configured in the Configure > Gateway > Interface > WAN
Interface: Display WAN1 or WAN2
Name: The name of WAN1 or WAN2
Connection: DHCP, PPPoE, or Static
Public IP: This is the Internet public IP address of the WAN interface seen by the EnGenius Cloud. If there is an upstream NAT device, then this is the public IP address of the NAT device. If the gateway WAN interface is directly connected to the Internet, then this is the native IP address of the WAN interface.
This graph shows the Latency between the EnGenius Security Gateway and Google Public DNS in a day/week/month view. Hover and click Day/Week/Month to see the latency graph view by Day/Week/Month.
The LAN tab displays the following information.
LAN Interface: the name of the LAN Interface
Subnet: the subnet IP address of the LAN Interface of the gateway
Used: the number of leased DHCP IP addresses of the gateway DHCP server for this LAN interface
The DHCP Lease tab shows the current DHCP leasing status of the gateway. The following information is displayed.
Client: the name of the DHCP client
MAC: the MAC address of the DHCP client
IP: the DHCP IP address of the DHCP client
LAN Interface
The following clients will not appear in the DHCP leases table:
Clients with statically assigned addresses
Clients with fixed DHCP assignments
Clients receiving an address from another DHCP server
Clients that have not successfully received an address from the EnGenius Gateway
you can access this page through Configure > Switches > Detail > VLAN
Using the VLAN tab, you can manually configure VLANs on the switch. Click Add to add another VLAN.
enter the VLAN ID and VLAN name of the switch.
Click the edit button to have the Port Assignment.
You can click the Tagged field or Untagged field to assign the tagged / Untagged port.
The (T) indicates the ports that will have Tagged data.
The (U) indicates the ports that will have data Untagged
If you used to input manually. You can click the pencil icon to input the port numbers.
Remember to click Apply to finalize the settings
For Apartments or other network environments, a network administrator might need to create VLANs for each unit, so needs to create hundreds of VLANs for the whole network switches. This will help the network admin to configure VLAN at a time instead of creating the VLAN one by one in each switch.
This will export the current VLAN JSON file of the switch and allows you to edit locally.
You can manually set up multiple VLANs for a specific switch by importing a JSON file.
Click the example hyperlink to download the JSON file
and then adjust the VLAN settings locally
then click JSON file upload to import your custom JSON file.
So you can import VLAN settings at a time instead use the current Web GUI to edit them one by one. Please notice that It will override your VLAN settings if you ever create the VLAN manually.
After a single configuration, you can go to another Switch VLAN setting page to import the same text file, so to save time to go over the creation.
As more and more devices are connecting to networks through Wi-Fi — laptops, phones, IoT devices, etc. And with all that wireless traffic, it’s becoming really important to control where those devices can go, especially when they try to access wired devices or the Internet.
That’s where the Layer 3 outbound firewall comes in. It gives us, as network admins, better control over outbound traffic from wireless clients.
With these firewall rules, we can decide whether to allow or block traffic going from Wi-Fi clients to the wired LAN or the Internet. This feature helps improve network security by managing outbound traffic from wireless clients to other network resources.
L3 firewall rules are defined to evaluate outbound traffic that is directed from wireless clients to the wired LAN or the Internet. The key components of how this works are as follows:
Top-Down Evaluation: Firewall rules are processed from top to bottom.
First Match Applies: The first rule that matches the traffic is applied, and all subsequent rules are ignored.
Default Rule: If no rule matches, the default rule is applied, which allows all traffic by default.
Stateless Behavior: L3 firewall rules are
A key L3 firewall rule is the "Private Address" default rule, which allows administrators to easily and quickly control whether wireless clients can access wired and wireless devices within private address ranges
A common use case for this rule is in a "Guest SSID" scenario. By changing the policy for traffic destined to the private address from Allow to Deny, clients on the guest SSID will be prevented from accessing the private address but will still be able to connect to the Internet. This feature works in both Bridge Mode and NAT Mode.
For this firewall rule, private addresses refers to any destination IP address within the private address spaces:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16
To configure the Private Address Deny rule, follow these steps:
Navigate to Configure > Access Point > Select SSID > Firewall
Click the Edit button and then change the "Policy" for the row with Destination as Private Address from Allow to Deny.
Click Apply to save changes at the top right of the page.
In this case, we want to block traffic from the 10.0.0.0/8 network to the 192.168.1.0/24 network but allow access to other remote networks like the Internet.
Here’s how it works with the rules:
Rule 1: Any traffic from 10.0.0.0/8 to 192.168.1.0/24 is blocked because it matches this rule with a "Deny" action.
Rule 2/3: The default rule allows all other traffic, so if traffic does not match Rule 1, it will be allowed.
As a result, traffic to the 192.168.1.0/24 network is blocked, while all other traffic — including Internet access and private addresses such as 172.16.1.1 — is still allowed.
Note: ESG510 Local Identify Type should change to IP address.
This guide is intended to help you set up your splash page. With a splash page, you can channel network users to see a custom page before they can access the Internet.
Before you start configuring a splash page, please make sure the captive portal is enabled in advance.
External Splash Page URL: The external splash page enables the administrator to host their own splash page web server, rather than having it hosted by EnGenius Cloud.
Local Splash page : Local Splash page provides the HTML for a splash page that will be hosted internally on the Access Point . For example , allows you to customize your splash page.
After you complete the splash page, please remember to click Apply.
You can choose different template from the drop-down menu at the top of the editor.
Once you select your starting template, you can customize it with your message, colors, fonts, and images. EnGenius uses a WYSIWYG (what-you-see-is-what-you-get) editor that also supports HTML editing.
In addition to the standard editing tools along the top toolbar , you can click HTML icon to start editing .
Choose a template from the drop-down menu at the top of the editor. You can customize the content and presentation of these templates to suit your needs . Any edits you make will be a copy of the template, you can go back to the default at any time.
Each splash page template comes with a library of stock images. You can also use the Insert Image tool to add your images and logos.
Click the Insert Image button, then navigate to a file, or drag and drop it into the upload images.
2.Double-Click on the image or click insert icon to add the image.
Once you created Orgs and Networks to define the scope of managed networks, next step is to add the devices to the managed network and manage them. To manage the Access Points in a Network, trigger the toolbar menu at the left-hand side: Manage > Access Points.
Click on Add from Inventory button. You can then pick the devices registered to the Org previously and add them to current Network.
For each camera, there are more settings available to configure and fine-tune the system. In addition, EnGenius Cloud collects and aggregates lots of data reported by camera periodically. Sophisticated graphs and tables are available on the camera detail page to ease the monitoring and tracking of a camera. To get all the details, on the cameras page, hover your mouse cursor on the row of cameras you are interested in. A Details button is shown, and click on it to get into the camera detail page. To reboot cameras, you can still hover on the row of cameras. and click on the Reboot button.
The first TAB page summarizes the camera's current settings and states. All details of configurations and statistics are shown on this page. On the top of the page, you can find the LED blinking button; this is used when you want to find where the camera is.
Before devices can be assigned to the network, they must be registered to an Organization that you preferred in advance.
Locate the serial number located on the bottom of the device.
2. Navigate to Organization > Inventory & License and click the Register Device on the top of the table.
3. Enter the serial number that you located in the device and enter them. If you have multiple devices you can enter the SN one per row, so devices could be registered at once. And then click the Register button.
Rule Number Limit: Each AP supports up to 256 user-defined Layer 3 firewall rules.

































WAN IP: The native IP address of the WAN interface. If the WAN interface is directly connected to the Internet, then this IP address is the same as the Public IP. If the WAN interface is connected to an upstream NAT device, then this IP address is usually a private IP address.
Gateway: the Gateway IP address of the WAN interface which is used as the next-hop gateway for Internet access through this WAN interface.
Expires in: the expiration time of the leased DHCP IP address
Clients connected over the client VPN
















Power on: this means the outlet is enabled but not connected to any device.
Powered off: this means the outlet is disabled and not able to provide power to the connected device.
Powered: this means the outlet is providing power to the connected device.
Click the outlet icon to view the outlet power and current usage history or reset the individual outlet.
The graph can be displayed based on different time intervals such as days, weeks, or months. Reset is only available when the outlet is enabled and never power off is disabled.
Name: Specify the outlet name.
Enabled: If you enabled the outlets, this means enabling full control of the outlets. Disabling the outlet means this outlet will be shut down and is not able to provide power to the connected device.
Never Power Off: The Outlet is always providing power. This function prevents users from accidentally powering off the outlet, which could cause the connected device to shut down suddenly. When enabled, the following happens:
The ability to power the outlet on or off via a time schedule is disabled.
The ability to power off the outlet from the LCD on the PDU is disabled.
The scheduled outlet reset function is disabled.
Rebooting the outlet will not stop it from providing power.
Pressing the power button on the PDU will not stop it from providing power.
Resetting the outlet from the LCD on the PDU will not stop it from providing power.
The autoreboot function will not work.
The hardware reset button is the sole method to disable the "never power off" function and deactivate the outlet. To perform a factory reset, press the button for 15 seconds.
Current: The measured electric current flowing through the device that is connected to the outlet. A current of zero amps means that there is no device connected to the outlet.
Consumed Power: Power consumption of the device that is connected to the outlet.
Power On Delay: Delays the outlet enabled time after the outlet has been powered on.
Power Off Delay: Delays the outlet disabled time after the outlet has been powered off.
Connected Device: the type of device connected to the outlet, which could be an EnGenius or non-EnGenius device. If an EnGenius device is connected, you can specify its model by clicking the chain icon and selecting the model name from the list.
Schedule: This will display what the outlet going to do according to the outlet scheduling.
Reset outlets: This will temporarily power off and power on the enabled outlet(s) that never power off is disabled.
Configures the following IP address settings:
IP Assignment: There are two IP assignments to choose from:
DHCP: Auto assigns the IP addresses if there is a DHCP server in the network.
Static: Manually assigns an IP address. The following fields need to be filled in:
IPV4 Address: PDU IP address.
Subnet Mask: PDU subnet mask.
Gateway: PDU default gateway.
DNS Server 1: Primary DNS server name.
DNS Server 2: Secondary DNS server name.

If Enabled "Contain all Rogue Devices", all rogue SSID devices will be contained automatically and Zero-Wait DFS will not be functional.
Scanning APs list down all APs who can do AirGuard (AirGuard AP), click “Details” will redirect to the AP detail page.
Users can set rules to categorize specific SSID or BSSIDs with a partial match or exact match.
All SSID match “Rogue rules”
All SSID match legitimate SSID but are not recognized by Cloud-managed device (It could be rogue AP, it also could be other vendors' legitimate AP)
Broadcast MACs are the BSSID (MAC), detected by our AP, broadcasting the rogue SSID. It could be multiple BSSIDs. Click on the line to see detailed information.
Seen by: the Rogue SSID might be detected by multiple EnGenius AP
Severity: The rogue reason severity could be high and require the user’s attention. The color bar in front of the SSID indicates the severity: Very high: Red; High: Orange…
Containment: Contained means the rogue SSID that your EnGenius AP is currently containing. Whenever a client attempts to connect to the rogue SSID, they will be forced off. Uncontained means the Rogue SSID is not currently contained.
Move to Whitelist: If the user found the SSID should be legitimate, then he can select it and move to whitelist (move to “Other SSIDs”)
Contain: This is the action that if you determine the Rogue SSIDs are threats to your network, you could click contain so the client will be forced off when the client attempts to connect the Rogue SSIDs.
Uncontain: This is the action that the Rogue SSIDs were noticed during a scan, but has not been determined to be a threat to your network, so you could click Uncontain.
More details:
AP impersonation: SSID = legitimate SSID and BSSID = legitimate BSSID, which means someone is using the legitimate AP’s MAC and SSID trying to steal client information
AP spoofing: BSSID = legitimate BSSID, but not legitimate SSID
The severity is always “Very High” and requires attention.
More details:
DoS attack trying to let clients or specific clients not able to connect to the AP
De-Auth attack: The rogue client sends a high volume of “De-Auth” traffic, so clients are always de-auth.
Dis-association attack: The rogue client sends a high volume of “Dis-association” traffic, so clients are always disassociated.
Attacked Party: Either specific client (MAC address) or broadcast (all MAC ff:ff:ff:ff:ff:ff)
More Details:
RF Jammer sends RF noise on a certain channel to increase the SNR rate or keep the SSID/channel busy, so the client cannot connect to SSIDs on the channel.
More details: https://docs.engenius.ai/whitepapers/airguard/rf-jamming
There are many BYOD devices (employee’s mobile phones) broadcasting SSID for their own use, which is harmless
Whitelisted SSID
Must Know:
One device can only be added to one network. All devices in the same network should apply the same network-wide settings except the settings are overridden individually.
Single click on the row of a AP (anywhere but hyperlink). It invokes a Quickview Panel that helps showing important status and key configurations for you. User can quickly finetune settings and do comparisons among different APs without going in and out different pages.
It's pretty common that for some cases you need to set channel or Tx power for specific APs. This would require the capability to override network's default radio settings.
Follow these steps to customize the radio settings for an AP.
Choose an access point from the list to show its expanded settings.
2. In the Radio section, click the checkbox below the lock icon to override default settings.
3.Configure the following settings for both the 2.4GHz and 5GHz radio band:
Channel
Tx Power
Channel Width
4. Click Apply.
Although APs in the same network share the same SSID settings, sometimes you just do not want a specific AP to enable all SSIDs in the network. For example, you don't want the SSID of financial department to be enabled and accessible everywhere. In the Quickview Panel, you can also finetune and override SSID settings.
Follow the steps to override network-wide settings and enable or hide the SSID of a network.
1. In the WLAN section, click on the checkbox near lock icon to override default settings.
2. Configure SSID to be enabled or hidden per your request.
3. Click Apply.
Once you have APs added to the network, you can apply more actions on the APs:
Move
Select one or multiple access points and click to move the AP(s) to another hierarchy view/network.
Remove
Select one or multiple access points and click to remove from the current org/hierarchy view/network.
People and Vehicle Counting help you to gain valuable insights into the number of people or vehicles that appear in a particular location.
This data can then be used to gain a better understanding of the traffic flow and density of persons or vehicles in the area, allowing for informed decision-making and better security planning
The will display whether the camera was recording video or not over a period of time. Green bars indicate the camera was recording on that period of time , The gray bar means the camera is not recording on that period of time
Place your cursor over each bar to see date, time, and recording status.
Traffic shows the camera Tx and Rx over a period of time
Brightness: Adjust the brightness level of the camera feed using the slider. The range is from 0% (minimum brightness) to 100% (maximum brightness). Increase the percentage to brighten the image, useful for low-light environments.
Contrast: Modify the contrast level to enhance differences between light and dark areas in the image. Use the slider to set a value between 0% (lowest contrast) and 100% (highest contrast).
Select the operating mode for the camera based on lighting conditions:
Auto: Automatically switches between day and night mode based on ambient light levels.
Always Day: Keeps the camera in day mode regardless of lighting conditions, ideal for well-lit environments.
Always Night: forces the camera into night mode, useful for consistently dark areas or nighttime surveillance.
Adjust the orientation of the camera image:
Normal: Standard orientation, suitable for most setups.
Upside Down: Flips the image vertically and mirror it too. Use this setting when the camera is mounted upside down.
Iris refers to the adjustable aperture of the camera lens that regulates the amount of light entering the camera sensor. Proper adjustment of the Iris ensures optimal image quality in varying lighting conditions.
Iris settings are critical to avoid issues like flickering, rolling effects, or over/underexposed images, depending on the environment where the camera is installed.
Fixed Mode: The Iris is set to its maximum opening, allowing the maximum amount of light to enter the sensor. Suitable for low-light environments where capturing as much light as possible is essential.
Indoor: Prioritizes eliminating flickering and rolling effects caused by indoor artificial lighting.
Outdoor: Auto-setting Iris to get best quality, but easy to meet rolling or flicker effect in indoor environment.
High dynamic range are camera techniques for capturing the same image at different exposures and then merging those images together to form a single image. This is particularly useful where the image consists of very light and very dark areas (e.g., an indoor camera that faces a window to outside).
Privacy Mask allows you to block sensitive areas from a camera’s feed. After you apply a privacy window to an area of the camera feed, subsequent video in the specified area is covered by dark.
RTSP streaming is for 3rd party applications, NVR, VMS, or NAS. Both live video and audio are streamed out at the same time.
Username/password : 3rd party application client needs them for Digest authentication during connection.
High Resolution URL: This is created automatically for copying to clipboard and being pasted in 3rd party applications.









The Client Timeline is a great feature that aggregates and analyzes activities of a specific wireless client to provide an intuitive and historical view. With Client Timeline, user can easily know how clients associate, authenticate, and roam among Access Points. It is extremely useful when you need to debug or trace your wireless network. The feature is available at Manage > Client > Client name.
The EnGenius Cloud AI system categorizes client activities into five different states:
Client was connecting to an AP. Client was roaming and connecting to another AP. Client changed to associate with different radio or SSID of the same AP. Client failed to authenticate with an SSID. Client was denied because of it is in block list.
The states are displayed at the left hand side of timeline. User can easily see how a client transited its states among APs.
The drawing and content of client timeline follows the color conventions as below:
Green: represent a 5G session.
Blue: represent a 2.4G session.
The communication between wireless client and AP could be very complicated. Different clients with different wifi chips and wireless drivers can behave very differently while communicating with the same AP. The intelligent engine behind Client Timeline is capable of analyzing communication packets effectively and performs clean and human readable transition details for the user.
User can click on the event summary inside a connection session to expand the sequence of transition details:
Table below displays client leave patterns when client leaves each connection session.
This section will provide device setup information to let users prepare ECW access points and ECS switches for device integration with EnGenius Cloud.
Power source option - An ECW AP device can be powered by an 802.3af/at-compliant PoE device or by DC12V input
Ethernet port:
LAN (PoE): Uplink port accepts an 802.3af/at power source.
LAN2: Data link if this port is built on a device.
Connect the AP to Internet:
You need to find a way to let the Cloud AP be able to access internet, so it can be managed by EnGenius Cloud.
Connect the uplink LAN port to a switch port or port of router: This is the most common way to let AP be able to access Internet. (Note: please make sure the port is internet accessible by connecting a notebook to the port and browse the internet)
Use your existing Cloud-managed ECW AP to mesh the new AP: Sometimes the place the AP installed is not accessible with Ethernet cable, then you can leverage EnGenius Mesh technology to mesh the new AP to your existing cloud-managed ECW AP.
After internet connected, you will see Power LED blinking until the AP is able to communicate with EnGenius Cloud and the LED becomes steady lid. Usually it will take about 8 mins if there is new firmware available to upgrade.
A) Connect the supplied power adapter (or power cord) to the switch and plug the other end into an electrical outlet. Verify the power LED indicator is lit on the switch. Wait for the switch to complete boot up. It might take few minutes to complete the process.
B) Connect one end of a category 5/6 Ethernet cable into the gigabit (10/100/1000) Ethernet port on the switch’s front panel and the other end to the Ethernet port on the computer. Verify that the LED on the Ethernet port of the switch is green.
The switch's default IP address setting is DHCP client mode, which will get an IP address from the DHCP server. It will automatically change to static IP address assignment if the switch cannot get an IP address from the DHCP server within two minutes of booting up.
If your switch cannot get an IP address from local DHCP server, or you would like to use static IP address assignment, you may follow the below procedures to manage your computer connection to the switch via a static IP address.
A) Once your computer is on, configure the settings of your network adapter. Open Network Connections > Local Area Connection > Internet Protocol Version 4 (TCP/IPv4) > Properties
B) Select Use the following IP address and make the following entries:
IP Address: 192.168.0.10 (or any address in the 192.168.0.x network)
Subnet mask: 255.255.255.0
A) Open a web browser on your computer. In the address bar of the web browser, enter the ECS switch IP address and hit enter.
B) The default username is admin and the password is password. We strongly recommend that you change these as soon as possible. Enter the username and password of the switch and then click Login.
*Your model number may be different in the web browser interface.
C) ECS Switch local access page will appear.
Video walls are for security to do daily monitoring of the cameras’ live video. It can be used on multiple displays through all cameras.
you can access this screen Manage > Camera > Video walls
Auto-create TV wall: Cameras remaining that are not on the existing TV wall will be added in order of camera name. They are put into the selected layout from top to bottom and left to right. TV walls and their names are generated automatically until all remaining cameras are added. The 4x4 layout is used in most situations, and this way saves a lot of setting time. Other layouts (3x3) and more tiles are optional for users to select.
Name : the video walls name
Layout: the video wall layout allows you to put the camera inside it.
After you create the video layouts, you can click Edit button to edit video walls details
Then click Add cameras button
Then drag the cameras inside the Video walls , then click Apply
This section describes the various firewall configuration options and capabilities of the EnGenius Security Gateway. You can access this page from Configure > Gateway > Firewall
Here you can configure permit or deny Access Control List (ACL) statements to determine what traffic is allowed between VLANs or out from the LAN to the Internet. These ACL statements can be based on protocol, source IP address and port, and destination IP address and port. These rules do not apply to VPN traffic. To configure firewall rules that affect traffic between VPN peers, please refer to Site-to-site VPN Settings
Site-to-site VPNs connect Multiple locations with static public IP addresses and allow traffic to be routed among the networks. This is most commonly used to connect an organization’s branch offices back to its main office, so branch users can access network resources in the main office.
Site-to-site VPN settings are accessible through the Configure > Gateway> Site-to-site VPN page
There are two options for configuring the EnGenius Gateway's role in the Auto VPN topology
(DS-Lite / MAP-E / IPIP)
This section describes how to configure IPv4 over IPv6 settings after selecting WAN1 as the connection interface. The EnGenius Gateway supports tunneling technologies such as DS-Lite, MAP-E, and IPIP to enable IPv4 communication over IPv6-based ISP lines.
In certain broadband environments, such as those provided by Virtual Network Enablers (VNEs), IPv4 connectivity is delivered over IPv6 infrastructure using tunneling technologies like MAP-E and IPIP (IP-in-IP). One widely used implementation of this model is commonly known as **v6plus**, which has been adopted by multiple ISPs to support high-speed access while preserving legacy IPv4 services.
Key characteristics of VNE-based IPv4 over IPv6 deployments include:





























The client was disconnected by the AP due to unknown reason.
Kicked by Cloud
The client was kicked by the cloud administrator.
Denied by ACL
The connection was refused by AP because the client was on the blocked list under access control.
Exceed client limit
The connection was refused because the client count has exceeded the maximum 2.4G/5G client limit.
Client inactive
The client was inactive because it was on power saving mode or far away from the AP.
Client disconnect
The client disconnected because the user disabled the Wi-Fi or choose to connect to other AP.
Disconnected due to SSID configuration change
The clients was disconnected due to SSID configuration change. Some configuration change took effect only after recycled (down&up) the NIC (network interface controller). When the NIC is down, all connection are disconnected.
Leaving reason
Description
Incorrect password
Client entered the incorrect password for WPA or wrong authentication information for EAP
Client switch to {device_name}/{radio}
When the RSSI signal is not good enough, the client did not disassociated from the AP and it connected to new AP directly with regular authentication procedure.
Roam out to {device_name}
When the RSSI signal is not good enough. The client disconnected from the original AP and connected to the new AP by 802.11r fast roaming protocol.
Steer to {radio}
The client disconnected from the AP due to band steering protocol. It received the 802.11v trigger and connected to suggested band accordingly.
Disconnected by {device_name}
The client was disconnected by the AP due to bad RSSI signal (fast handover).
AP disconnect
If the LED keeps blinking, then there could be some issues like no IP address, or local proxy server setting required...etc. To set static IP or Proxy, or managed VLAN, you can login to Local Access Page through Managed SSID of the AP.
In this mode, the EnGenius Gateway acts as a layer 3 routing gateway between WAN and LAN interfaces. Client outbound traffic to the Internet is source Network Address Translated (NATed) with the gateway’s WAN1/WAN2 IP address. As a layer 3 routing gateway, LAN-to-LAN traffic passing through the gateway can also be bridged or routed and can be controlled by outbound firewall rules as well.
In this mode, the EnGenius Security Gateway acts as a layer 2 bridge that does not perform any routing or network address translation for client outbound traffic for Internet access. This mode is usually used when you want to put the EnGenius Security Gateway between a customer's existing external NAT device and an internal L2/L3 switch. And you want to deploy EnGenius Security Gateway to provide firewall filtering and VPN services without changing the existing IP subnet address planning.
EnGenius Security Gateway can support dual WAN(WAN1/WAN2) configurations for dual WAN load balance and redundancy. Below are the WAN1 configuration settings. For the connection type, the Interface can be configured to DHCP to dynamically obtain an IP address or to static IP to manually configure the IP address or to use PPPoE to authenticate the gateway to an Internet Service Provider (ISP)
Name: the WAN Interface Name
DHCP: When you select DHCP, the gateway will automatically configure its IP address, subnet mask, and default gateway for the WAN interface.
PPPoE: Point-to-Point Protocol over Ethernet (PPPoE) is a specification used to authenticate a networking device to an Internet Service Provider (ISP). Selecting PPPoE will allow you to enter the following information:
Username: Enter the username associated with your ISP. This is a required field.
Password: Enter the password associated with your ISP. This is a required field.
DNS Server: you can choose the DNS server from ISP or use Google Public DNS (8.8.8.8) or specify nameservers entered in the Primary DNS and Secondary DNS.
VLAN id: Enter the VLAN id from 1-4094.
ISP Bandwidth: you should check with your ISP (Internet Service Provider) for the actual Download/Upload bandwidth. The ISP Bandwidth is used in WAN link utilization and dual WAN outbound sessions load balance calculations.
EnGenius Security Gateway can support dual WAN(WAN1/WAN2) configurations for dual WAN load balance and redundancy. To deploy dual WAN configuration, you have to enter the following WAN2 settings. After WAN2 is enabled and settings configured here, the WAN2/P3 port will act as the WAN2 port.
Primary WAN Interface: either WAN1 or WAN2 can be selected as the Primary WAN Interface in a dual WAN configuration deployment.
Load Policy:
Failover: When both WAN1 and WAN2 are up, only the Primary WAN is active for inbound and outbound services. If the Primary WAN is down, automatic WAN failover will occur then the other WAN will take over and become active for services.
Load balance: For inbound services, the usage and restriction are the same as Failover. for the client's outbound Internet access traffic sessions, when both WAN1 and WAN2 are up, both WAN1 and WAN2 are used for outbound connections. The session load balance distribution algorithm is based on WRR(Weighted Round Robin) using WAN1/WAN2 upload bandwidth.
Cellular networks are high-speed, high-capacity voice and data communication networks with enhanced multimedia and seamless roaming capabilities for supporting cellular devices. With the increase in popularity of cellular devices, these networks are used for more than just entertainment and phone calls. They have become the primary means of communication for finance-sensitive business transactions, emergency services, etc. WAN connectivity options, such as cellular networks, now also serve as a reliable backup internet uplink in the event of a primary uplink failure. You can plug in the USB modern in the EnGenius Gateway and configure the following settings.
SIM PIN: Enter the Security Code on the SIM to prevent unauthorized use of the card.
Dial on Demand: Only connect when traffic is sent over the interface.
Idle timeout: If there is no traffic on the interface for the given minutes, the gateway will disconnect the link.
We offer the EnGenius Security Gateway that supports Dynamic DNS (DDNS) service by default. With this feature, users can have a hostname associated specifically with the ESG WAN interfaces. ESG uses Dynamic DNS (DDNS) to update a registered DNS hostname A record automatically each time its Primary WAN IP address changes. This feature is useful because it allows the administrator to configure applications such as client VPN to access the EnGenius Gateway by its hostname which is static instead of an IP address that may change over time. When the Primary WAN is down, EnGenius Security Gateway will use the public WAN IP of the other WAN for DDNS update.
DDNS Enable: click the button to enable/disable the DDNS service.
DDNS Providers: Select your DDNS service provider from the pull-down menu, if your DDNS service provider is not in the list, please select Custom
Username: input your registered username
Password: input your registered password
Hostname: input your registered DDNS FQDN hostname
Enter other required information from your DDNS Service Provider

Click Add a rule to add a new outbound firewall rule.
The Protocol field allows you to specify TCP traffic, UDP traffic, ICMP traffic, or Any.
The Policy field determines whether the ACL statement permits or blocks traffic that matches the criteria specified in the statement.
The Src.IP and Dest.IP fields support IPs or CIDR subnets. Multiple IPs or subnets can be entered comma-separated.
The Src. Port and Dest.Port fields support port numbers. Multiple ports can be entered comma-separated. You can enter additional information in the Description field
Apply to all ESG in the org: It is used when you want to have the same firewall rules in all gateways in one organization. so the outbound rules will be replicated to all EnGenius Gateway in the same Organization.
You can create firewall rules to block specific applications without specifying IP addresses or port ranges. This feature is particularly useful when applications frequently change their IP addresses or use multiple IPs
Click Add a rule to add a new outbound firewall rule.
You block entire categories and specific applications within a category. For instance, you can block all Steaming or Apple music/spotify while allowing business-critical ones
This allows you to generate a documented record of your outbound firewall rules in a CSV format. This documentation serves various purposes, including backup, future reference, and troubleshooting.
You can click on the Export button located at the top right corner to export current Outbound rules in a CSV format.
Use this option to forward traffic destined for the WAN IP of the EnGenius Gateway on a specific port to any IP address within a local subnet or VLAN. Click Add rule to create a new port forward. You need to provide the following:
Protocol: TCP or UDP.
Public IP: Listen on the Public IP of WAN 1, WAN 2, or WAN1 & WAN2.
Public port: Destination port of the traffic that is arriving on the WAN.
LAN IP: Local IP address to which traffic will be forwarded.
Local port: Destination port of the forwarded traffic that will be sent from the EnGenius Gateway to the specified host on the LAN. If you simply wish to forward the traffic without translating the port, this should be the same as the Public port.
Allowed remote IPs: Remote IP addresses or ranges that are permitted to access the internal resource via this port forwarding rule.
Description: A description of the rule.
This allows you to generate a documented record of your port forwarding rules in a CSV format. This documentation serves various purposes, including backup, future reference, and troubleshooting.
You can click on the Export button located at the top right corner to export current Port forwarding rules in a CSV format.
Use this option to map an IP address on the WAN side of the EnGenius gateway (other than the WAN IP of the EnGenius Gateway itself) to a local IP address on your network. Click Add a 1:1 NAT mapping to create a new mapping. You need to provide the following:
Uplink: The physical WAN interface on which the traffic will arrive.
Public IP: The inbound destination public IP address that will be matched to access the internal resource from the WAN.
LAN IP: The IP address of the server or device that hosts the internal resource that you wish to make available on the WAN.
Rules: You can add rules to specify the matching conditions that only incoming connections matching the following conditions are accepted for 1:1 NAT service to access internal LAN resources.
Allowed Remote IPs: Enter the source IP addresses/ranges that will be matched. You can specify multiple WAN IP addresses/ranges separated by commas.
Protocol: Choose from TCP, UDP, ICMP, or any.
Public Ports: Enter the destination port that will be matched. You can specify multiple ports separated by commas.
Creating a 1:1 NAT rule does not automatically allow inbound traffic to the public IP listed in the 1:1 NAT mapping. By default, all inbound connections are denied. You have to configure matching Rules as described above in order to allow the inbound 1:1 NAT traffic.
This allows you to configure the allowed services to access EnGenius Gateway
ICMP Ping: Use this setting to allow the EnGenius Gateway to reply to inbound ICMP ping requests coming from the specified address(es). Supported values for the remote IP address field include None, Any, or a specific IP range (using CIDR notation). You can also enter multiple IP ranges separated by commas.
Web (local status & configuration): Use this setting to allow or disable access to the local management page via the WAN IP of the EnGenius Gateway. Supported values for the remote IPs field are the same as for ICMP Ping.
This feature allows users to log specific firewall rules for monitoring and troubleshooting. Logs can be stored in a syslog server or accessed in real-time to analyze network activities.
Go to Gateway > Firewall > L3 outbound firewall rules or 1:1 NAT or port forwarding rules.
Check Syslog to identify which rule you need to save in the Syslog server or do real-time log download, then apply.
Those rules can be logged to syslog server but need to make sure you configured syslog server IP address in configure > general Settings > networks
When pressing Real-time logs, it will pop out to download real-time log (10~60 seconds) information (PS: real-time log needs wait gateway configuration status is up to date)

Hub (Mesh): This EnGenius Security Gateway acts as a VPN Hub(Mesh) node and will establish VPN tunnels to all remote EnGenius VPN peers in the same organization that are also configured in this mode. It will also establish VPN tunnels to Spoke nodes that specify this gateway as their common Hub node.
Spoke: This EnGenius Security Gateway acts as a VPN Spoke node and will establish only one tunnel to the specified remote EnGenius Security Gateway which acts as this gateway’s Hub node. All Spoke nodes with a common Hub node can reach each other through Hub-and-Spoke tunnels unless blocked by Site-to-Site VPN firewall rules.
If you have multiple LAN subnets, you have the option to specify which LAN Interface could participate in the VPN.
If the EnGenius Gateway is behind a firewall or other NAT device, there are two options for establishing the VPN tunnel:
Automatic: In the vast majority of cases, the EnGenius Gateway can automatically establish site-to-site VPN connectivity to remote EnGenius VPN peers even through a firewall or NAT device using a technique known as "UDP hole punching". This is the recommended (and default) option.
Manual: Port forwarding: If the Automatic option does not work, you can use this option. When Manual: Port forwarding is enabled, EnGenius VPN peers contact this EnGenius Security Gateway using the specified public IP address and UDP port number 500. You still need to configure port forwarding rules on the upstream NAT/firewall device to forward all incoming traffic with the specified destination IP and destination UDP 500 and UDP 4500 to the Primary WAN IP address of the EnGenius Security Gateway.
Auto VPN(Mesh VPN or Hub and Spoke VPN) works on EnGenius Security Gateways in the same organization only. For the following conditions, you must use the Add Non-EnGenius Gateway option.
To establish a Site-to-Site VPN connection between an EnGenius Security Gateway and a 3rd party VPN device.
To establish a Site-to-Site VPN connection between 2 EnGenius Security Gateways in 2 different organizations.
Click "Add " and enter the following information
Gateway Name: A name for the remote gateway
Public WAN IP: The Primary WAN public IP address of the remote gateway.
Private Subnet: Enter the local network address or subnet behind the remote gateway.
IKE Version: What IKE version to use (IKEv1 or IKEv2).
Local ID: Enter the identity of the remote gateway during authentication. Only IKEV2 needs this ID.
Remote ID: Enter the Remote ID of the remote peer. The remote Gateway’s Primary WAN public IP is recommended. Do not enter the remote peer’s Primary WAN native private IP if it is behind an external NAT device.
IPsec Policy: Select a pre-defined policy or have a custom one.
Diffie-Hellman group: Select which Diffie-Hellman group you want to use for encryption keys
Encryption: Select which key size and encryption to use.
Authentication: Select between MD5 and SHA1 authentication. Only phase2 can be multi-selected.
PFS key Group: Select the Off option to disable Perfect Forward Secrecy (PFS). Select groups 1, 2, 5, or 14 to enable PFS using that Diffie Hellman group.
Lifetime: Type the maximum number of seconds that the IKE security association can last.
Pre-shared Key: Enter the pre-shared secret key to use.
You can add firewall rules to control what traffic is allowed to pass through the VPN tunnel. These rules will apply to outbound VPN traffic to/from all EnGenius Gateway in the Organization that participates in site-to-site VPN. These rules are configured in the same manner as the Layer 3 firewall rules described on the Firewall Settings page of this documentation. Note that VPN Firewall rules will not apply to inbound traffic or to traffic that is not passing through the VPN.

The list of clients can be customized based on time intervals, and the chart can be customized based on time intervals and SSIDs. To change these parameters, use the appropriate dropdown menu at the top of the screen.
You can search for a client in the current client list by using the search. You can search by any parameter included in the search options, and it will attempt to match your query across all fields. You can also specify multiple parameters by clicking on the icon in the search box, as seen below:
This allows you to block clients on the current SSID that clients connected.
Once you want to unblock clients, please go to Configure > SSID > Access control to delete the Mac Address from the Block list.
This allows you to make clients VIP on the current SSID or on Network-wide that clients are connected.
Once you want to delete clients from the VIP list, please go to Configure > Access control to delete the Mac Address from the VIP list.
If you don't want to block clients permanently, you could just kick them so that they can connect again if they want to.
This will display the clients that are directly connected to the downlink port on switches.
This will display clients that are assigned by the Gateway DHCP server.
You can also see this information regarding the client:
MAC Address - The MAC address of the client device in the packets sent from the device.
IP - Assigned IP address of the client device.
Hostname - Host Name of the client device.
OS - Operating System that the device is Running.
After configuring the client VPN and users are starting to connect, it may be useful to see how many and which client devices are connected to your network. To see connected client VPN devices, navigate to Manage > Clients > VPN Client
You can also see this information regarding the client:
Name: the name of the VPN client.
VPN IP: the IP of the VPN client.
Remote IP: the external IP of the VPN client.
The Bluetooth Client feature in EnGenius Cloud allows you to monitor nearby Bluetooth-enabled devices detected by EnGenius APs.
Favorite
Mark important devices with a star for quick reference.
Name
Shows the Bluetooth device name (if available).
MAC Address
The Bluetooth MAC address of the device.
Last Seen
The time the device was last detected
Last Seen by AP
The specific AP that last detected the device. Clickable link to AP detail page
Vendor
The manufacturer of the device (if identifiable). Otherwise shown as “Other.”
- IPv4 access via MAP-E or IPIP - Optional static IPv4 assignment (typically with IPIP) - Integration with DDNS and authentication mechanisms - Routing and tunnel management handled by the VNE infrastructure
After selecting WAN1 under Configure > Gateway > Interfaces > WAN, choose a connection type:
- IPv4 over IPv6 (DS-Lite) - IPv4 over IPv6 (MAP-E) - IPv4 over IPv6 (IPIP)
For DS-Lite, configure the following parameters:
Field
Description
BR / AFTR Address
Required. Provided by ISP.
DNS Server
Fixed to “From ISP”.
MAP-E is a stateless tunneling method and does not require manual configuration.
Field
Description
DNS Server
Fixed to “From ISP”.
For IPIP-based deployments, select a VNE type: v6plus or Xpass. Each has distinct parameter requirements.
Field
Description
BR / AFTR Address
Required. Provided by ISP or VNE.
IPv4 Address
Required. Static IPv4 address.
Interface ID
Assigned by v6plus.
Update Server URL
Provided by provider.
Username / Password
Optional, depending on ISP.
DNS Server
Fixed to “From ISP”.
Field
Description
BR / AFTR Address
Required. Provided by ISP.
IPv4 Address
Required. Static public IP.
DDNS Update Server URL
Required. Provided by Xpass.
Basic Auth ID / Password
Provided by Xpass.
FQDN / DDNS ID
Assigned hostname.
DDNS Password
Provided by Xpass.
Under Configure > Gateway > Interfaces > LAN > Addressing, enable IPv6 using one of the following options:
- Disable - Auto (DHCPv6-PD) - Auto (IPv6 Relay)
Both IPv4 and IPv6 addresses will display in:
- Manage > Gateway List - Manage > Gateway Detail
LAN allows you to partition your network into different subnets such that downstream hosts are separated into different broadcast domains based on the VLAN they operate in. VLAN-based network separation can be an effective tool for isolating and identifying different segments of your network and therefore provides an additional layer of security and control. The EnGenius Gateway can have multiple LAN IPs, each of which is the default gateway address on its particular VLAN.
You can access this page through Configure > Gateway > Interface > LAN
There are two modes for the LAN Interface
The ESG can support a single Bridge and multiple VLANs. The same LAN port can be added to both a bridge and VLAN simultaneously.
the ESG provides the flexibility to operate in multiple untagged subnets (Bridges) and multiple tagged subnets (VLANs) on the LAN side. If you want to have multi-untagged subnet environments, you can use Multiple bridge mode. However, The same LAN port cannot be added to both a bridge and VLAN simultaneously.
Select the "Multiple Bridge"
Add another interface and set Bridge mode
Verify the Untagged subnets if this is OK
To add a new Interface, click Add Interface at the top right of the LAN table. To modify an existing LAN, click the Interface name in the LAN table.
You can click the LAN interface name to access the below screens.
Name: Enter the LAN interface name
IP address: Use this option to enter the IP subnet and IP address of the gateway for the LAN Interface. For example, if the IP subnet is 192.168.100.0/24 and the gateway's IP Address is 192.168.100.1/24, please enter 192.168.100.1/24.
Use VPN: Determines whether the EnGenius Gateway advertises this LAN Interface to site-to-site VPN peers.
Port: select the port to use the LAN Interface.
The EnGenius gateway provides a fully-featured DHCP service when configured in Routed mode on the Configure > Gateway > Interface > WAN > Operation mode page. You can enable and configure the DHCP service on each LAN Interface individually, You can access this screen on the Configure >Gateway > Interface > DHCP page.
The configuration options include:
Client Addressing: Choose Run a DHCP server to enable DHCP services on that particular VLAN
DNS Servers: DNS servers that the DHCP server will instruct the clients to use
Reserved IP range: IP ranges that are reserved and therefore will not be assigned to clients.
Lease Time: Specify the DHCP address lease time, the default is 1 day. You can select 30 minutes,1 hour, 4 hours, 12 hours, 1 day, and 1 week.
Additional Options: Specify additional DHCP options sent to the DHCP client by clicking +Add
The Largest DHCP pool the EnGenius Gateway will serve is equivalent in size to a /19 subnet, even on a LAN configured with a larger subnet.
If you want to forward DHCP requests for a configured subnet or VLAN to another DHCP server rather than serving DHCP on the EnGenius Gateway, you can do so by choosing the Relay DHCP to another subnet DHCP server option for Client addressing and entering the IP address of the DHCP server you wish to forward requests to.
The DHCP relay server must be reachable in one of the following three ways:
The DHCP server is in a local VLAN configured on the EnGenius Gateway
EnGenius Gateway's DHCP server in all LAN interfaces is disabled.
The DHCP server is in a subnet for which a static LAN route is configured on the EnGenius Gateway.
There are 2 options, Click-through and Custom RADIUS (External)
Click-through: After a client opens and enters a URL on his/her browser, the Client browser will be redirected to a Captive Portal splash page without username/password authentication required. But the client must view and acknowledge the splash page before being allowed to access the network.
Custom RADIUS (External): After a client opens and enters a URL on his/her browser, the client will be redirected to a Captive Portal splash page where username/password authentication is required before being allowed to access the network. An external RADIUS server must be set up to authenticate the client’s username/password. Enter the following settings for your gateway to access external RADIUS servers for authentication. You can configure 2 RADIUS servers for redundancy.
Server 1: IP address, Port number, and shared secret
Server 2: IP address, Port number, and shared secret
NAS ID: For NAS(Network Access Server) ID, please enter an ID for your gateway to access the RADIUS servers specified.
NAS IP: For NAS(Network Access Server) IP, please enter a VLAN IP address of your gateway for your gateway to access the RADIUS servers specified as the source IP address.
Select one of the 2 options below to redirect the client after successfully passing the Cut-through splash page or the Custom RADIUS (External) splash authentication page.
Redirect to the original URL: Select this option to cache the initial website from the client during the authentication process and then forward it to the originally targeted web server after the user successfully authenticates.
Redirect users to a new URL: Select this option to redirect users to a pre-designated URL after the user successfully authenticates.
Session Timeout: Specify a time limit after which users will be disconnected and required to log in again.
Idle Timeout: Specify a time limit for an idle client after which users will be disconnected and required to log in again.
Walled Garden: This option allows users to define network destinations that users can access before authenticating. For example, your company's website.
With a splash page, you can channel LAN users to see a custom page before they can access the Internet.
You can click to see the details
“Incorrect device configurations pushed by the EnGenius Cloud, such as incorrect VLAN configuration, incorrect IP address settings, incorrect management VLAN configuration,configuration file incompatibility after firmware version upgrades”,or “Unexpected software or hardware anomalies in devices, such as system failures, insufficient memory, application/protocol crashes, and uplink port problems", often result in lost connection from the EnGenius Cloud. As usual, the ONLY solution is for an operator to go ON-SITE to directly connect to the device for further configuration and troubleshooting. This not only wastes manpower but also results in prolonged downtime for the device, leading to network instability for downstream devices.
To enable devices to automatically attempt to resolve issues without on-site support,rapid fault recovery, reduce labor costs, and minimize downtime, we have introduced an automatic self-healing mechanism for EnGenius devices. This mechanism can attempt to (1) rollback configuraiton to a previous stable configuration or (2) reboot the device if it loses connection to the cloud. It can gracefully handle connectivity issues, providing an opportunity for administrators to quickly address urgent network disconnections.
Stable Configuration is a key feature of EnGenius Cloud, designed to ensure connectivity stability after configuration updates. When EnGenius Cloud pushes a new configuration to a device, it may result in the device losing connection. To resolve connectivity issues as much as possible, the primary purpose of Stable Configuration is to quickly revert to the previous stable connection settings (Stable Configuration) after EnGenius Cloud push configuration to the device and a disconnection occurs.
Therefore, whenever a new configuration is pushed to the device, it will go through a series of state machines to determine if this new configuration can become the next stable configuration, as illustrated in Figure 1.
Stable configuration is generated when a device remains connected to the cloud and has not rebooted within 30 minutes after an EnGenius Cloud push configuration change to the device. Essentially, a stable configuration is the latest configuration pushed by EnGenius Cloud that has not resulted in a lost connection or been followed by a reboot within the subsequent 30 minutes.
Step 1. EnGenius Cloud pushes configuration to EnGenius device at T1 time.
Step 2. After the configuration is pushed, if the device meets the following requirements for 30 consecutive minutes, it will proceed to Step 3. Otherwise, the device will enter a Self-healing mechanism:
(1) Remains connected to the cloud
(2) Does not reboot
Step 3. The EnGenius device will copy the running configuration applied at T1 time to the stable configuration.
Activating the device's automatic self-healing mechanism can gracefully handle "lose connection to the cloud" and help administrators quickly resolve urgent device connection issues.
For EnGenius Gateway: Loss of WAN connection: Unable to ping 8.8.8.8/domain continuously for 2 hours.
For EnGenius AP/Switch/PDU/Extender: Gateway ARP unreachability: Continuous failure in the gateway ARP reachability test / inability to ping the Gateway for 2 hours.
When the device loses connection to the cloud, the EnGenius device will activate different Self-healing mechanisms depending on the cause of the disconnection: (1) pushed configuraiton by cloud or (2) other issues unrelated to cloud push settings, such as device malfunctions, etc., to restore the connection. We expect that the device will reconnect to the EnGenius Cloud after the self-healing process.
(1) Pushed configuraiton by cloud
When the cloud pushes a configuration to the device, and the new configuration has not yet become a stable configuration, the device may lose connection. Since this situation is often caused by incorrect configuration settings leading to disconnection, the device will activate a self-healing mechanism to revert to the Stable Configuration state prior to the erroneous settings, as illustrated in Figure 2.
Step 1. EnGenius Cloud pushes configuration to EnGenius device at T2 time.
Step 2 and Step3. If (1) EnGenius device loses connection and has not restored connectivity within 2 hours, and (2) the new configuration applied at T2 time has NOT become the stable configuration, EnGenius devices will activate a Self-healing mechanism to revert to the previous stable configuration, such as the one applied at T1 time.
Step 4. When the device reconnects to the cloud, it will send an event log to EnGenius Cloud containing information about reverting to the stable configuration.
(2) Other issues unrelated to cloud push settings Before disconnection, if the device is in a stable connection state, the running configuration will be copied as the stable configuration. In this lost connection situation, it could indicate an issue with the upstream network equipment or a problem with the device's own system or hardware.
For EnGenius Gateway: it will attempt to reboot once after 8 consecutive hours of lost connection to restore normal operation, as illustrated in Figure 3. Rebooting the gateway will restore the EnGenius Gateway system (software & hardware) to a healthy and stable state, including CPU, memory, and application operations. Once rebooted, the EnGenius gateway may reconnect to the Cloud, and all downstream devices on the gateway's LAN side may return to their normal routing paths, resolving urgent issues.
Step 1. EnGenius Gateway loses connection.
Step 2. When the device is in a Stable State, it means the Stable Configuration is the same as the running configuration, and then EnGenius gateway loses connection with the cloud for 8 consecutive hours.
Step 3. EnGenius Gateway will active a Self-healing mechanism and Reboot the device once.
Step 4. Send an event log to EnGenius Cloud to log that the "Reboot" action was activated by the self-healing mechanism when reconnected to the Cloud.
For EnGenius APs, Switches, PDUs, and Extenders:
EnGenius Switch/AP/extender/PDU will NOT reboot.
Network administrators often need to further troubleshoot issues due to connection losses often caused by other netwrok devices in the path between the AP and its gateway. For instance, if an AP can't connect, they should check for failures or routing problems between the AP and its gateway.
When an EnGenius device rollbacks to a "Stable Configuration" via an activated Self-healing mechanism and reconnects to the cloud, users can be notified/ know through the following methods:
Event Log - Navigate to ANALYZE > Device Event to view the Event log with Rollback Configuration Type.
- An additional "Rollback Configuration" Type can be used for filtering.
Alert Click the bell/alert icon in the top right corner to view the event log of the rollback configuration.
Email When the event of the rollback configuration occurs, if the user has enabled email notifications, the EnGenius Cloud will
Cloud Configuraiton on Local Status Page(LSP) When the device rollback to a stable configuration, it may still be in a lost connection state, or the upstream connection may be unable to access the internet, preventing the user from entering EnGenius Cloud to troubleshoot the issue. Users can access the Local Status Page (LSP) to check the current configuration status. Users can also check the “Cloud Configuration” field on the LSP page to see if the Self-healing mechanism has been activated to revert the device to its Stable Configuration.
Once the device has been restored to a Stable Configuration through the self-healing mechanism, users and FAEs can access the change log page & Event log page to track configuration changes in chronological order, as the Stable Configuration includes timestamps.
When the device moves to another network, all rollback data & Stable Configuration will be erased and reset to default values.
AP: v1.x.85
Switch: v1.2.100
Extender: v1.0.25
Gateway: v1.2.65
PDU: v1.0.25
In NAT mode, the EnGenius APs run as DHCP servers to assign IP addresses to wireless clients out of a private 172.x.x.x IP address pool behind a NAT.
NAT mode should be enabled when any of the following is true:
Wireless clients associated to the SSID only require Internet access, not access to local wired or wireless resources.
There is no DHCP server on the LAN that can assign IP addresses to the wireless clients.
There is a DHCP server on the LAN, but it does not have enough IP addresses to assign to wireless clients
The implications of enabling NAT mode are as follows:
No NAT client can be talked to the other NAT client, neither same SSID nor different SSID (client isolation enabled and block internal routing)
Change the IP range of CP DNS to be same as AP DNS (172.16-23.0.0/16)
NAT mode works well for providing a wireless guest network since it puts clients on a private wireless network with automatic addressing.
When an SSID is configured in NAT Mode, wireless clients will point to the access point as their DNS server. The AP then acts as a DNS proxy and will forward clients' DNS queries to its configured DNS server.
This allows you to set custom DNS servers for a NAT SSID, instead of using the AP's DNS server. This is typically used to forward NAT SSID clients to a DNS server with custom content filtering.
1. Navigate to Configure > SSID, then choose one SSID to customize the DNS settings.
2. Locate the Client IP mode and choose NAT mode then click Custom DNS.
3. Enter the preferred Custom DNS IP addresses.
4. Click Apply.
In bridge mode, the APs act as bridges, allowing wireless clients to obtain their IP addresses from an upstream DHCP server.
Bridge mode should be enabled when the following is true:
Wired and wireless clients in the network need to reach each other (e.g., a wireless laptop needs to discover the IP address of a network printer, or wired desktop needs to connect to a wireless surveillance camera).
The implications of enabling Bridge mode are as follows:
Wired and wireless clients have IP addresses in the same subnet
Bridge mode works well in most circumstances, particularly for Roaming. and is the simplest option to put wireless clients on the LAN.
1. Navigate to Configure > SSID , then choose one SSID.
2. Locate the Client IP mode and choose Bridge mode then click Apply.
the EoGRE (Ethernet over GRE, or Layer 2 GRE tunnel ) is to build a GRE tunnel between AP and the remote site, so all traffic of the “EoGRE-enabled” SSID will go through the encrypted tunnel to the remote service center
When SSID’s EoGRE is enabled, all traffic of connecting clients will be tunneled by EoGRE to forward to TGW (Tunnel Gateway)
The connected client then sends a DHCP request to TGW to get an IP address
Option 82 can be enabled to provide more information for the DHCP server to assign IP accordingly.
DHCP option 82 (also known as the DHCP relay agent information option) is used to prevent DHCP client requests from untrusted sources. The DHCP relay agent will insert more information of “circuit ID” to identify the request is from, say, which AP BSSID (radio mac), which SSID name, and which VLAN ID…, so the DHCP server can identify if the request is from an authorized source, and bases on the information to assign IP.
Circuit ID usually includes which ESSID (SSID name) and VLAN ID the client is connecting to. Remote ID usually includes which AP (AP MAC and BSSID - Radio MAC) is relaying the DHCP requests.
Users can define the fields to add to the Circuit ID and Remote ID. EnGenius Option 82 provides options as below:
AP Ethernet MAC
AP Radio MAC
SSID Name
SSID Type
1. Navigate to Configure > SSID , then choose one SSID.
2. Locate the Client IP mode and choose Tunnel (EoGRE).
3. Choose the VLAN (the default value of “VLAN” is SSID default VLAN. If the value is changed, then it will override the SSID default VLAN ).
4. Input the Tunnel Gateway IP ( the IP of the remote site the GRE tunnel will be connecting to ).
5. Decide to enable the DHCP option-82, if yes, Input Delimiter ( how the field is separated in the option 82 frames) and select the Circuit ID and Remote ID and then click Apply.

For each AP, there are more settings available to configure and fine-tune the system. In addition, EnGenius Cloud collects and aggregates lots of data reported by AP periodically. Sophisticated graphs and tables are available on the AP detail page to ease the monitoring and tracking of an AP. To get all the details, on AP list page, hover your mouse cursor on the row of AP you are interested in. A Details button is shown and clicks on it to get into AP detail page.
The first TAB page summarizes AP's current settings and states. All details of configurations and statistics are shown on this page.






















DNS Server
Fixed to “From ISP”.










































NAS Port: For NAS(Network Access Server) port, please enter a port number for your gateway to access the RADIUS servers specified as the source TCP port number.










App Notification When the event occurs, if the user has enabled Mobile App notifications, EnGenius Cloud will immediately send App notification to the administrator.
Configuration Status on the Device’s Detail page Navigate to MANAGE > AP/Switch/Gateway/PDU/Extender > Select Specific Device > Click Details. Users can view the configuration status through this.
Configuration Status on the Device’s Status in Device’s list page. For the detail, user can see "Configuration Rollback" Status and please refer to Device status" in the Device Status and Warning Enhancement section.







VLAN ID




The SSID section allows you to check and configure the exact SSID settings for this AP.
SSID: shows the SSID name.
Radio: shows the Radio (2.4GHz or 5GHz bands) turned on in this AP.
Security: security type set on the SSID.
Captive portal: shows authentication type for captive portal.
The Throughput section allows you to check the throughput statistics for this AP. Note that you can control the filters to get different results based on your requirement:
By SSID
By Time (daily/weekly/monthly)
The Radio section allows you to configure individual radio settings. The default radio setting will be followed by the network radio setting. If you want the radio settings of an access point to be different from the default, you can override them with custom values.
Enables customization of RSSI thresholds for specific APs to address unique scenarios. This will override the settings located on Configure Radios > Fast Handover
This section allows you to configure IP address settings for the AP individually.
DHCP: You can choose to auto assign IP addresses if there is a DHCP server in the network.
Static: Allows you to manually assign an IP address.
Enter the IP address you wish to assign to the access point and fill in the subnet mask, default gateway, and DNS server address.
IPV4 Address: Enter the IP address for the access point.
Subnet Mask: Enter the subnet mask for the access point.
Gateway: Enter the default gateway for the access point.
DNS Server 1: Enter the primary DNS server name.
DNS Server 2: Enter the secondary DNS server name.
When an AP is just installed, you can take a photo (or several) on the AP and uploaded it to EnGenius Cloud as a property data for the AP. It's helpful for the installer to memorize where and how he installed the AP.
The EnGenius Cloud Log contains several logging subsystems that each have unique data retention and export options available. Datasets like device event, system configuration, and analytics are used for starkly different purposes (business intelligence, operations, risk management, etc.) and are reflected in the native logging capabilities. In the Log TAB page, the system list all the device logs for current AP. If you need to track events across a network, check Device Events for more details.
While the device log provides a thorough timeline of events on the AP, it is usually unnecessary to view all events. The following options are available to filter down the event log as needed.
Filtering events to a specific client can help troubleshoot individual connectivity issues. Entering the MAC address, hostname, or custom name in the Client field will display only events affecting that client, excluding other client information and device events. For the same reason, SSID field can be used to filter out events related with other SSIDs.
The event log shows all events for clients and devices, starting with the most recent event by default. The date and time filters are useful to display only events that happened at or before the specified time.
The event log are categorized in different severity:
Error
Warning
General
You can also set the filter to only show the logs with dedicated severity.
The following types of events will be reported by ECW access points:
WLAN Client Connection
WLAN Client Control
WLAN Radio
Client Roaming
Device Status
Mesh
AirGuard
The filter also support all types of events listed above.
Clients page provides comprehensive details of wireless clients that ever managed by the access point.
This page is filtered for current AP and supports all features as same as in Managing Clients. To get more details, please refer to the Managing Clients section.
EnGenius Cloud provides powerful diag tools to track every details of your network in REALTIME. To trigger the Diag Tools, simply click on the diag button shown below:
Please refer to Diag Tools to get more details.
On the top of AP detail page, the are two buttons available to control AP LEDs instantly.
LED Light: This allows you to enable or disable all LEDs on the AP. This is helpful if users does not want to LEDs of AP interfering their vision at night.
LED Blinking: Click light bulb icon. LEDs on the AP will blink for 10 seconds. This helps the installer to find and identify a AP.
RSSI
Signal strength indicator.



























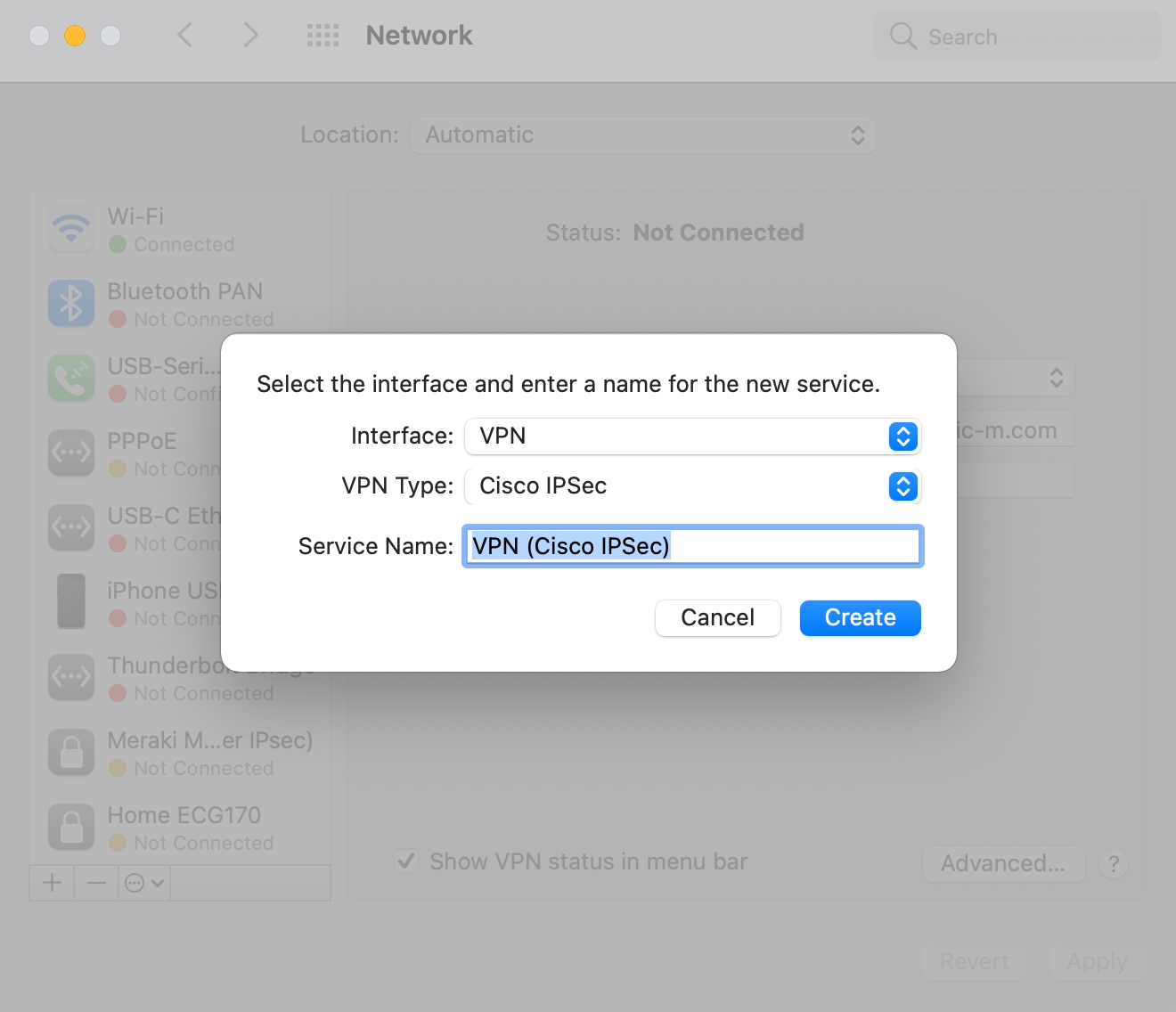




















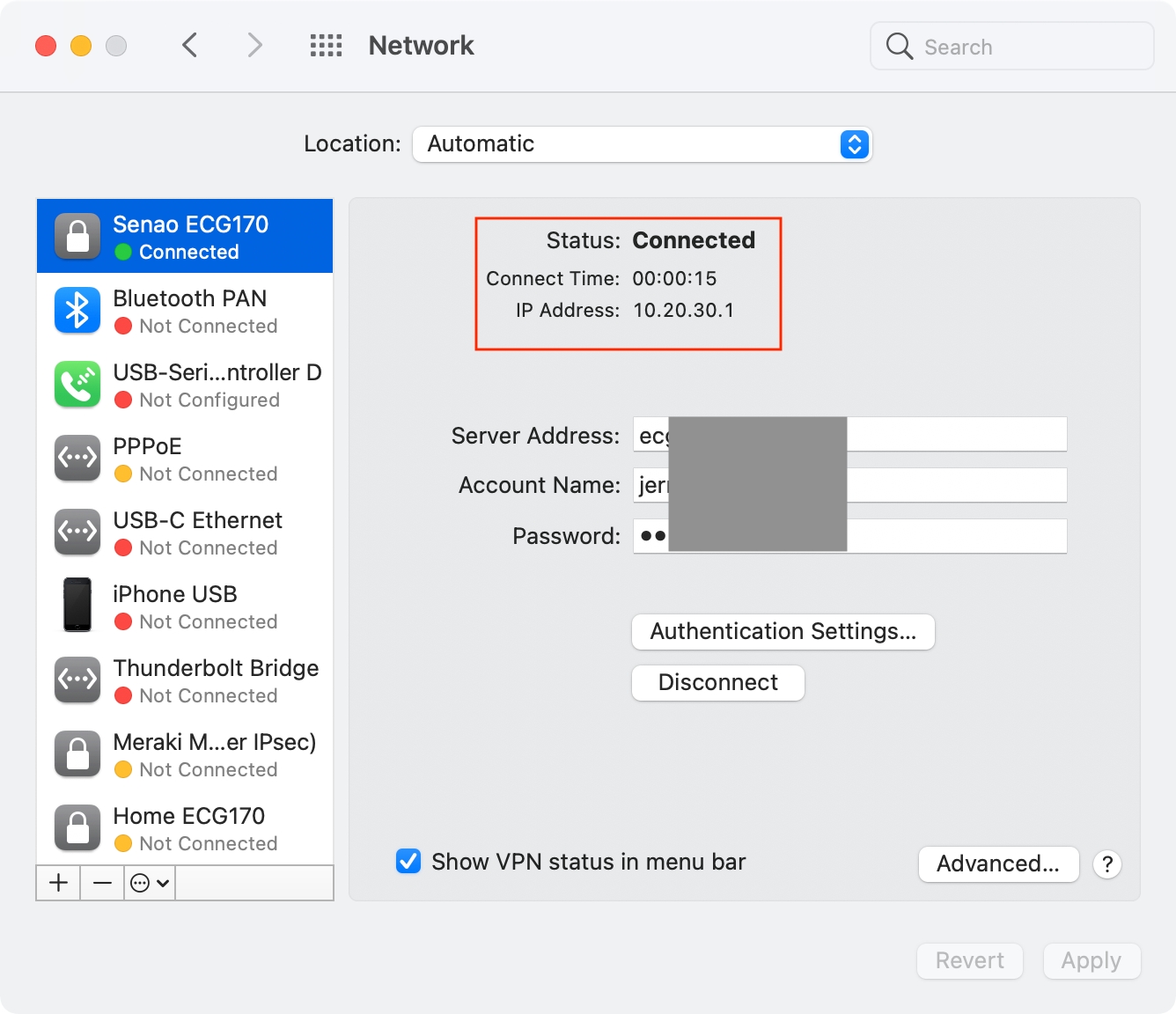


































The LCD panel on the front of the PDU allows you to quickly access information about the PDU and its outlets. When you power on the PDU for the first time, the EnGenius logo will appear, followed by a QR code. You can scan the QR code to access the PDU quick start guide.
To access the Home page, long press the bottom of the control buttons beside the LCD panel. The Home page shows the current PDU usage, including the usage percentage, wattage, electric current, and voltage. The usage percentage is divided into four levels to indicate the overall power consumption status:
Green: Low usage.
Orange: Moderate high usage.
Red: High usage.
Dark red: Critical usage.
You can check the usage of each outlet by pressing the upper control button. Pressing the upper control button again will show the usage of the next outlet. The following screenshot shows the Outlet 6 details of an EnGenius switch (the model name is ECS1008P) that is plugged into the PDU.
The next time you power on the LCD panel, the Home page will be displayed automatically.
See below for how to use the LCD panel.
See below for the different icon definitions.
To access the Menu, complete the following steps:
Go to the Home page.
Press the lower control button.
To navigate through the options, use the upper control button, which functions as the Next button. To view the details of a selected topic, use the lower control button as the Enter button. In some cases, you may need to drill down further to view more specific details.
The following shows the available options displayed on the Menu.
Displays the following information when an Outlet is selected.
Press Menu > Outlets > (Select an outlet).
Peak Data: Recorded the highest current and power usage over a specific time interval.
Data Interval: Frequency at which the PDU collects and reports power/current usage information. This information is used to create the line charts in Peak Data.
Enable: Enables the outlet, so outlet is able to provide power to the connected device.
Disable: Disables the outlet, so the outlet will be powered off.
Reset: This will temporarily disable and enable the outlets.
Displays the power on / power off/ reset time on the schedule for each outlet.
Press Menu > Schedule
Displays the alert message for each outlet.
Press Menu > Alert
Displays the PDU details, which include the IP address, MAC address, software version, and time zone.
Press Menu > Information
Displays the following configurable display settings:
Press Menu > Display Settings
Orientation: Configures the content on the screen to be presented in a horizontal or vertical orientation.
Theme: Choose between a dark or light theme for the content display.
Screen saver: the idle time that the LCD will turn off.
Displays the QR code to view the PDU quick start guide or product web page.
Press Menu > QR Code
Reboots the PDU. The outlets still provide power during a PDU reboot.
Press Menu > Reboot
The PDU will be restored to its default settings, and all the data will be deleted. The power supply will be temporarily interrupted until the reset process is completed.
Press Menu > Factory Reset
From the Switches page, you can click Details on the web interface to display detailed information about a switch.
PoE reset from the Switch Panel : User can mouse-over to the PoE port of the switch port panel and power-cycle the port, so the device attached to the port will be rebooted
Total PoE Usage: This bar graph displays the consumed, remaining, and total wattage utilized by Power over Ethernet.
Total PoE Utilization by Port: Displays the current PoE utilization by each port, in watts.
The System Settings section allows you to configure all primary networking options for your switch.
A Spanning Tree Protocol is a Layer 2 protocol that prevents loops in a network with redundant paths created by multiple switches. We recommend using this feature if your environment incorporates multiple switches.
Enable the STP option
Select a Protocol
Select a Bridge Priority value
Click Apply
The Link Layer Discovery Protocol (LLDP) is a Layer 2, vendor-neutral protocol that allows network devices to advertise capabilities, identity, and other information. This data can potentially be queried by SNMP.
Enable the LLDP option
Click Apply
The Voice VLAN feature configures switches to automatically allow and prioritize voice traffic over a designated VLAN. This keeps voice traffic separate and prioritized over other traffic types.
Mode: Allows you to define the Voice VLAN mode.
Auto: Automatically advertises the Voice VLAN to connected devices via the LLDP-MED protocol.
OUIs: Determines whether a received packet is a voice packet by checking its source MAC address.
Switch Voice VLAN: Allows you to choose what VLAN is used for Voice VLAN. You can set up VLANs in Port Settings.
QoS Priority: Lets you define whether the switch will use the Quality of Service CoS value of the incoming packet, or tag the packet with a CoS value between 1-7.
OUIs: VoIP traffic has a pre-configured Organizationally Unique Identifier (OUI) prefix in the source MAC address. You can manually add a specific manufacturer's MAC address and description to the OUI table. All traffic received on the Voice VLAN ports from the specific IP phone with a listed OUI is forwarded on the voice VLAN.
Quality of service (QoS) allows operators to prioritize application traffic to ensure that latency-affected data, such as VoIP and video conferencing, is uninterrupted during periods of network congestion. Switches implement this by reading tagged packets and prioritizing them accordingly. Packets are classified using Class of Service (CoS) on the data link layer, and Differentiated Services Code Points (DSCP) on the network layer, mapped to a queue, then sent out accordingly as per QoS.
Trust Mode: Allows you to define whether the switch will use CoS, DSCP, or both trust modes for QoS.
Scheduling Method: Allows you to define what method the switch will use when assessing transmitting incoming packets in queues. Strict priority always prioritizes queues with a higher priority, while Weighted Round Robin (WRR) weights each queue by priority, then applies a round-robin policy when choosing packets for transmission. The queues are weighted as follows:
Queue Mapping: Tagged packets are sent to queues defined in this setting. For each CoS or DSCP value, you can choose the queue to which tagged packets are mapped.
IGMP Snooping is used for controlling multicast traffic. It listens to IGMP messages being processed by the switch and prevents these messages from being sent to hosts not part of the respective multicast.
Version: The available IGMP Snooping versions are v2 and v3. You can select either/or in the Version dropdown.
VLANS: You can enable IGMP Snooping for any VLAN by selecting the corresponding checkbox next to the VLAN ID.
Ethernet has used the 1500 byte frame size since its inception. Jumbo frames are network layer PDUs that have a size much larger than the typical 1500 byte Ethernet Maximum Transmission Unit (MTU) size. Jumbo frames extend Ethernet to 9000 bytes, making them large enough to carry an 8 KB application datagram plus packet header overhead. If you intend to leave the local area network at high speeds, the dynamics of TCP will require you to use large frame sizes.
The switch supports a jumbo frame size of up to 9216 bytes. Jumbo frames need to be configured to work on the ingress and egress port of each device along the end-to-end transmission path. Furthermore, all devices in the network must also be consistent on the maximum jumbo frame size, so it is important to do a thorough investigation of all your devices in the communication paths to validate their settings.
Jumbo Frame : Enter the size of a jumbo frame. The range is from 1522 to 9216 bytes.
Selecting one or more ports and clicking Configure will display the following settings:
Enabled: Allows you to enable or disable the connection for this port.
Label: Allows you to add a descriptor for this port.
Speed/Duplex: Allows you to define the following speed/duplex communication settings for this port:
Auto: Speed/Duplex will auto-negotiate based on the connected node.
1Gbps / Full Duplex
100 Mbps / Full Duplex
100 Mbps / Half Duplex
Power over Ethernet (PoE): Allows you to power a connected device through an Ethernet cable using your switch.
VLANs: Allows you to group devices to create a partitioned network on the same LAN.
Forward Ports: By configuring the forward ports, ports can be separated into different groups where traffic between different group are blocked.
Rate Limit: Allows you to limit the amount of incoming and outgoing traffic in Mbps.
Flow Control: Enabling this will have the switch regulate traffic during times of congestion.
QoS: If QoS is enabled in Switch Settings, you can configure additional settings per port.
CoS Value: All incoming packets that lack a CoS value will use the one set in this dropdown.
Trust CoS: If checked, the switch will queue packets tagged with CoS into their designated queues. If unchecked, all packets will leave the same queue.
VLAN Trunking: This allows the specific ports to receive/forward VLAN without adding this port to the member port of a specific VLAN. please notice that VLAN trunking will override the current VLAN port member setting except management VLAN.
System setting is followed by Switch setting from the Configure > Switch settings as default settings. If you want individual AP System settings to be different from the Switch Network- wide setting , you can click below part in the screen to override the setting .
Use this screen to configure radio settings for all access points in the network.
Double-click one of the networks on Org-Trees > Configure > Radio Settings.
The settings and options in the Radio Setting page apply to all access points in a network, and you can configure the following settings:
This option allows users to customize the allowed channels while adhering to country-specific regulations.
When you click “Select DFS Channel,” all DFS channels will be automatically selected from the auto-channel selection list.
When you click “Deselect DFS Channel,” all DFS channels will be automatically deselected from the auto channel selection list.
Some use cases may require that Dynamic Frequency Selection (DFS) channels be excluded from the Auto Channel algorithm. DFS channels can be allowed or excluded on the radio settings page.
Since DFS channels can only be used until radar communication is heard, disabling DFS may be useful if the wireless network is in close proximity to a harbor, airport, or weather radar station. Administrators may also want to disable DFS if most local wireless clients do not support DFS channels.
With 1200 MHz of spectrum and 59 new 20 MHz channels, a station with a dwell time of 100 ms per channel would require almost 6 seconds to complete a passive scan of the entire band. The standard implements a new efficient process for clients to discover nearby access points (APs). In Wi-Fi 6E, a process called fast passive scanning is being used to focus on a reduced set of channels called preferred scanning channels (PSC). PSCs are a set of 15 20-MHz channels that are spaced every 80 MHz. The APs will set their primary channel to coincide with the PSC so that it can be easily discovered by a client, and clients will use passive scanning in order to just scan PSCs to look for an AP.
PSC Disable: When PSC is disabled, all 6G channels will be available in the interface, allowing users to select any channel freely.
PSC Enable: When PSC(Prefered Scanning Channel) is enabled, channels are grouped into sets of four for easier selection, based on the minimum 80 MHz spacing requirement.
The use of 40 MHz channels on the 2.4 GHz band does not provide for multiple independent channels in multi-AP deployments for 2.4GHz. The recommended setting is 20MHz. To maximize throughput, use 40 MHz for 802.11n and 80 MHz for 802.11ac for 5GHz. Note that higher density deployments should use 20 MHz or 40 MHz channels on 5 GHz.
Using this option, users can set a custom range for Tx power.
The higher the transmission power (Tx power) of the access point, the bigger the coverage of the WiFi signal, so usually maximum power is set for an access point to connect to another access point for WDS or mesh purposes.
However, it might not be the best practice if the access point serves the purpose of being a client access point because usually client devices (notebooks, mobile phones, etc.) might not have the same transmission power to be able to communicate back.
The current device's transmission power can be referenced , where most notebooks and mobile phone transmission power range from 15dBm - 25dBm. Some WiFi devices, like Amazon Echo, are in the smaller range of 10-11dBm.
If your enterprise environment is comprised mainly of notebooks and mobile phones, then it is better to turn down your access point transmission power to 15-17dBm on 5G, and 10-12dBm for 2.4G (so the coverage area of 5G and 2.4G is about the same). If you keep the same transmission power of 5G and 2.4G, it also means the signal strength of 2.4G is about 6 dB higher than 5G at the same location. Then the client device might roam from 5G to 2.4G because it detects better signal strength. It is highly recommended to leverage the EnGenius ezWiFiPlanner tool to simulate coverage with different transmission power settings.
EnGenius access points can adjust the minimum bit rate for each radio (2.4G and 5G separately). When the minimum bitrate is set, an access point will send out beacons based on the minimum bit rate.
For example, if the bit rate is set to 6Mbps, then those clients with slower than 6Mbps bit rate will not be able to connect to the WiFi and will not slow down other clients' performance. 802.11b max bit rate is 11Mbps, so if 12Mbps is set per radio, then 802.11b clients will not be able to connect to the network.
The other benefit is to help better roaming, because when a client roams to a weaker RSSI signal and causes slower performance, then the access point will be kicked out, and the client will search the available SSIDs again to connect to a stronger signal SSID.
If the value is set too high, then it also means a greater density of access points are required to cover the area with the minimum bit rate. This may potentially cause more channel conflict because the transmission power of the access point remains the same, so the RF coverage area is the same and more RF areas overlap.
This is a hardware limitation, commonly applied to most access points in the market. There can be 254 clients connected to an access point at a maximum (127 clients to each 2.4G and 5G band). To serve more than 127 2.4/5G clients in a space, a higher density of access points must be deployed.
This option allows users to discard 802.11 a/b/g devices to use network to prevent the impact of performance on other 802.11ac/ax clients.
Some legacy wireless clients are not compatible with 11ax. This option allows legacy equipment to connect with your network as usual, we suggest you disable 11ax in 2.4G of your Radio settings. In this way, you can have equipment working in 5G with better performance and get legacy devices served well in 2.4G.
Some legacy wireless clients are not compatible with 11be. This option allows legacy equipment to connect with your network as usual.
Disabling RTS/CTS can reduce additional signaling overhead and latency, thereby increasing data transmission efficiency, especially in environments with strong signals and minimal interference, such as in directional antennas.
Dynamic Channel Selection allows a Wireless Access Point to monitor traffic and noise levels on the channel which is current operating and also keeps watching utilization of other channels with background scanning.
When DCS is enabled and traffic or noise levels of current channel exceed predefined threshold (50%) for a period (15 mins), the AP ceases operating on the current channel and hops to an alternative channel with best utilization in statistics. If you want to schedule the DCS, you could expand the advanced settings and select 2 timeslots in a day or do the DCS every time interval.
DCS is useful for the complex and dynamic wireless environment where numerous APs and travel routers broadcast and transmit packets in the same area. It usually comes with high radio interference and the situation changes from time to time. In this case, DCS could be helpful to react for unexpected interference with a short-term mechanism and jump to a cleaner channel to operate.
After you enable Client Balancing, AP will use information about the state of the network and wireless protocol 802.11V to steer the clients to the best available access point during association. Require firmware v 1.x.20 or above, and only support on ECW220v2/ECW220v3.
This option will allow users to enable meshing on the 2.4GHz, 5GHz or 6GHz bands. Auto Pairing will assist in wirelessly connecting (meshing) to an access point (AP) that is not connected to a LAN connection.
Once you enable mesh and click Apply, an Auto Pairing button will appear. The Auto Pairing button will trigger access points that are connected to the internet to scan and mesh with neighboring access points that are not connected to the internet.
Locate an AP that is wired and connected to a LAN (i.e., connected to Cloud, Power LED is steady orange).
Place the new unwired AP, which is already registered to an organization (Org) and assigned to a network, within 10 meters of the LAN-connected AP.
3. Power on the new unwired AP and the “mesh” LED will begin flashing.
4. Click the Auto Pairing button under Radio Settings in cloud to begin the meshing process. The connected AP will attempt to find and mesh with the new unwired AP.
a. There must be a cloud-connected AP nearby for the new AP to wirelessly connect.
b. All APs must be on the same “network” so that the mesh configuration can be pushed to all
APs in the mesh group.
c. It will take approximately 4-10 minutes for an AP to complete the meshing process due to
firmware upgrade and reboot.
5. Once complete and successful, the mesh LED will be on, and the power LED will be blue on all
mesh-connected APs.
In wireless network, roaming issues often stem from sticky clients—devices that remain connected to an access point (AP) with a weaker signal, even when a closer AP with stronger signal strength is available. This behavior negatively impacts both network performance and user experience.
To address this issue, Fast Handover leverages configurable mimimun RSSI thresholds to assist devices in seamlessly roaming between APs, ensuring stable and optimized connectivity.
Since Received Signal Strength Indication (RSSI) reflects the signal strength of a wireless client, adjusting the Minimum RSSI threshold allows administrators to set the minimum signal strength required for a client to stay connected to the AP. This ensures that clients maintain stable and optimized connectivity.
If a client’s signal strength drops below the Minimum RSSI:
Force Disconnection: Disconnects clients with RSSI below the configured threshold, encouraging them to connect to a better AP.
Block Weak Signal Connections: The AP will prevent client with weak signals from connecting, helping to optimize network resources.
RSSI Threshold Parameters
The Fast Handover feature supports three configurable RSSI thresholds on each band:
Probe Request Threshold: Minimum RSSI required for a client to send a probe request to the AP.
6
Control Button for Callout 4
1
Status icons
2
PDU information
3
Action icon
4
Action icon
5
Control Button for Callout 3








































32
7
64
8
128
10 Mbps / Full Duplex
10 Mbps / Half Duplex
1
1
2
2
3
4
4
8
5
16


6
Forced Disconnect Threshold: Minimum RSSI required to maintain a connection; clients are disconnected if they fall below this value.
Enable/Disable Options
Each threshold can be independently select RSSI Value or disabled:
Select RSSI Value : Activates the threshold, enforcing RSSI-based restrictions.
Disable: Removes the threshold, allowing unrestricted connections.
Configuration Levels
Network-wide Configuration: Applies unified RSSI settings across all APs to ensure consistent roaming behavior.
Location: Go to CONFIGURE > Access Point > Radio Settings and adjust the Fast Handover settings.


























Flash (quick)
Error or Disconnected
Orange
Flash (quick)
Firmware Upgrading
Orange/Blue
Flash
Flash
No LAN Physical Connection
LAN LED
Green
Off
LAN Connected
LAN LED
Green
Solid On
LAN Transmitting
LAN LED
Green
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Green/Green
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Green/Green
Flash
Mesh Backbone Good
LAN LED
Green
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Green
Flash twice upon 1 sec off
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Flash (quick)
Error or Disconnected
Blue
Flash (quick)
Firmware Upgrading
Blue/ Light Green
Flash
Flash
No LAN Physical Connection
LAN LED
Blue
Off
LAN Connected
LAN LED
Blue
Solid On
LAN Transmitting
LAN LED
Blue
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Blue/Bllue
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Blue/Blue
Flash
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Blue
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Blue
Flash twice upon 1 sec off
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Flash
No LAN Physical Connection
LAN LED
Blue
Off
LAN Connected
LAN LED
Blue
Solid On
LAN Transmitting
LAN LED
Blue
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Blue/Blue
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Blue/Blue
Flash
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Blue
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Blue
Flash twice upon 1 sec off
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Flash
No LAN Physical Connection
LAN LED
Blue
Off
LAN Connected
LAN LED
Blue
Solid On
LAN Transmitting
LAN LED
Blue
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Blue/Blue
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Blue/Blue
Flash
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Blue
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Blue
Flash twice upon 1 sec off
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Flash
No LAN Physical Connection
LAN LED
Blue
Off
LAN Connected
LAN LED
Blue
Solid On
LAN Transmitting
LAN LED
Blue
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Blue/Blue
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Blue/Blue
Flash
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Blue
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Blue
Flash twice upon 1 sec off
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Flash
No LAN Physical Connection
LAN LED
Orange
Off
LAN Connected
LAN LED
Orange
Solid On
LAN Transmitting
LAN LED
Orange
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Green/Green
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Green/Green
Flash
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Orange
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Orange
Flash twice upon 1 sec off
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Flash
No LAN Physical Connection
LAN LED
Blue
Off
LAN Connected
LAN1/LAN2 LED
Orange(1Gbps) Green(2.5Gbps)
Solid On
LAN Transmitting
LAN1/LAN2 LED
Orange(1Gbps) Green(2.5Gbps)
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Green/Green
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Green/Green
Flash
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Blue
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Blue
Flash twice upon 1 sec
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Flash
No LAN Physical Connection
LAN LED
Blue
Off
LAN Connected
LAN LED
Blue
Solid On
LAN Transmitting
LAN LED
Blue
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz /6GHz
Blue/Blue/Blue
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz / 6GHz
Blue/Blue/Blue
Flash
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Blue
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Blue
Flash twice upon 1 sec
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Power LED
Orange
Flash
No LAN Physical Connection
LAN LED
Blue
Off
LAN Connected
LAN LED
Blue
Solid On
LAN Transmitting
LAN LED
Blue
Flash
Wi-Fi Interface On / Off
2.4GHz / 5GHz
Blue/Green
Solid On / Off
Wi-Fi Transmitting
2.4GHz/ 5GHz
Blue/Green
Flash
Mesh Connection On / Off
Mesh LED
Blue
Solid On / Off
Mesh Auto Pairing
Power LED
Orange
Flash (1.5 sec on -> 0.5 sec off -> duration for 8 min)
Mesh Backbone Good
LAN LED
Blue
Flash (0.5 sec interval)
Mesh Backbone Weak
LAN LED
Blue
Flash twice upon 1 sec off
Firmware Upgrade
Power LED
Orange
Flash
Reset to Default
Power LED
Orange
Flash
AP Locating (LED Blinking)
Power LED
Orange
Flash (1.5sec On -> 0.5sec Off -> duration for 10sec)
Status
LED Color
State
Power Up AP
Orange
Static
Waiting Period (before being added to Cloud)
Orange
Flash (slow)
Connected to Cloud
Blue
Static
Reset to Default
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Status
LED Color
State
Power Up AP
Blue
Static
Waiting Period (before being added to Cloud)
Blue
Flash (slow)
Connected to Cloud
Light Green
Static
Reset to Default
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected
Status
LED / Color
State
Power On /Off
Power LED
Orange
Solid On / Off
Cloud Connected
Power LED
Orange
Solid On
Connecting to Cloud
Power LED
Orange
Flash
Cloud Disconnected










Blue
Power LED
Orange
Light Green
Power LED
Orange
Power LED
Orange
Power LED
Orange
Power LED
Orange
Power LED
Orange
Power LED
Orange
Power LED
Orange


